Digital Signing in the Cloud

Digital Signing in the Cloud
In digital signing, we use our private key to sign for a message, and then the proof of signing is done with our public key. This happens for a Bitcoin transaction, and where we take the private key from our wallet and then sign for a transaction. The public key is then used to prove that the user signing the transaction.
Generating the signing key pair
With digital signing we often use ECDSA. With this, Bob uses his private key to sign a hash — along with a nonce value (k), and produces a signature (r,s). This is passed to Alice and who takes the message, Bob’s public key, and the signature, and can determine if the signature is correct:
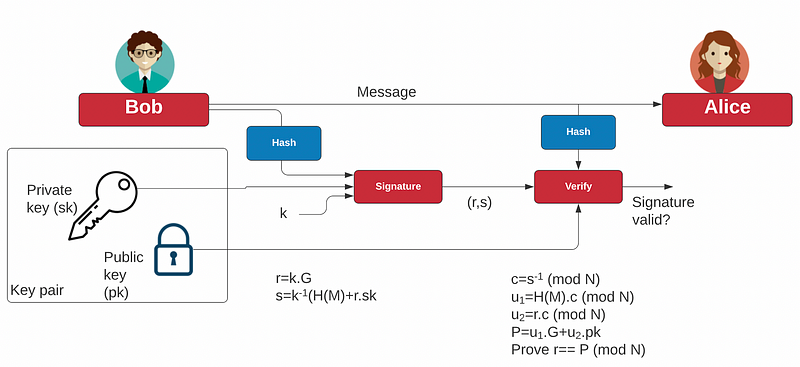
Creating an elliptic curve key pair
Initially, in AWS, we create a new customer-managed key:

We then select a public key (asymmetric) and one which can sign and verify:

In this case, we are using the NIST ECC P256 curve. Next, we create an alias for the key:

Next, we define the administrative permissions:

And for key permissions:

Finally, we have our key created:

Signing a message with the private key
We can first create a file (1.txt):

With this, we will use the “aws kms sign” command.
$ aws kms sign --key-id alias/MyPublicKeyForSigning \
--message fileb://1.txt --signing-algorithm ECDSA_SHA_256 \
--query Signature > 1.outThis will produce a Base64 output for the signature:
cat 1.out
"MEUCIDCLKoExmRW6lRs73EC3Gd2lEvlqCEvNhiezw10ZRrn3AiEA8KSQ4oiIR0bKhPh+SX9IxRO0xhLZTKFwYwe3v1OATT8="In order to check the signature, we need to convert this format into binary:
$ base64 -i 1.out -d > 1.sigIf we list the signature file (1.sig), we can see it is in a binary form:
$ cat 1.sig
0E 0*1@ݥK͆']F!∈GFʄ~IHLpcSM?We can now verify the signature using the message (1.txt), the public key and the signature file (1.sig):
$ aws kms verify --key-id alias/MyPublicKeyForSigning \
--message fileb://1.txt --signature fileb://1.sig \
--signing-algorithm ECDSA_SHA_256
{
"KeyId": "arn:aws:kms:us-east-1:960372818084:key/2ebd6d65-59f4-4bbb-a661-f929011d9a41",
"SignatureValid": true,
"SigningAlgorithm": "ECDSA_SHA_256"
}And you can see that the signature has proved to be valid. If we change the file:

And then try again, and we will get an exception:
$ aws kms verify --key-id alias/MyPublicKeyForSigning \
--message fileb://2.txt --signature fileb://1.sig \
--signing-algorithm ECDSA_SHA_256
An error occurred (KMSInvalidSignatureException) when calling the
Verify operation: Signatures in Python
With Boto3, we can then convert the CLI implementation into Python. For this we use the sign() and verify() methods in boto3, and then use the SigningAlgorithm=’ECDSA_SHA_256'. We use a ECC key pair, and which is “2ebd6d65–59f4–4bbb-a661-f929011d9a41”:
import base64
import binascii
import boto3
AWS_REGION = 'us-east-1'
def enable_kms_key(key_ID):
try:
response = kms_client.enable_key(KeyId=key_ID)
except ClientError:
print('KMS Key not working')
raise
else:
return response
def sign(msg, alias):
try:
sig = kms_client.sign(KeyId=alias,SigningAlgorithm='ECDSA_SHA_256',
Message=bytes(msg, encoding='utf8'),
)
except ClientError:
print('Problem with encryption.')
raise
else:
return base64.b64encode(sig["Signature"])
def verify(msg, ciphertext, alias):
try:
plain_text = kms_client.verify(KeyId=alias,
SigningAlgorithm='ECDSA_SHA_256',
Message=bytes(msg, encoding='utf8'),Signature=bytes(base64.b64decode(ciphertext)))
except ClientError:
print('Problem with decryption.')
raise
else:
return plain_text['SignatureValid']
kms_client = boto3.client("kms", region_name=AWS_REGION)
KEY_ID = '2ebd6d65-59f4-4bbb-a661-f929011d9a41'
kms = enable_kms_key(KEY_ID)
print(f'Public Key KMS ID {KEY_ID} ')
msg='Hello'
print(f"Plaintext: {msg}")
sig=sign(msg,KEY_ID)
print(f"Signature {sig}")
val=verify(msg,sig,KEY_ID)
print(f"Verified: {val}")A sample run is:
Public Key KMS ID 2ebd6d65-59f4-4bbb-a661-f929011d9a41
Plaintext: Hello
Signature b'MEUCIF8nyHSZYusVDw7oFV+SQND/gfW6m8EGO6NMO9TsbXbeAiEAooyOjYMVOjd0Gz9UXYGmp0ZwAp3nWxC2CQxPekQOOvI='
Verified: TrueConclusions
Digital signing allows us to verify the creator of a message, and where the private key is used to sign the message, and then proven with the associated public key.
Here are the details: