And So Shamir Cracked Merkle’s Knapsack … But Along Came Naccache and Stern (and it’s uncracked!)

And So Shamir Cracked Merkle’s Knapsack … But Along Came Naccache and Stern (and it’s uncracked!)
I recommend to any early career researcher that they find a new paper which is having a good impact to read, and also read a classic paper. For this week, my classic paper has been the Naccache Stern Knapsack cryptosystem for public key encryption, and it took me back to the time that Merkle and Hellman created a public key method which was eventually cracked by Adi Shamir. The crack left the field clear for the RSA method to become the de-facto public key method.
David Naccache and Jacques Stern
RSA has survived over four decades and is still going strong. But, there have been other methods for public key encryption that have not quite scaled the levels of RSA. And, so, in 1997, David Naccache and Jacques Stern produced a knapsack method for public key encryption, and which has still to be broken [1][here]:

Before we cover the Naccache-Stern Knapsack cryptosystem, we will first cover the method created by Ralph Merkle and Marty Hellman [2]:

Knapsack encryption provides a good approach to creating public and private keys, where their private key is easy to use, while the public key is difficult to compute. Within five years of the paper being published, Adi Shamir [3] cracked it, and so RSA was clear to become the de-facto method:

The Knapsack problem
The knapsack problem defines a problem where we have a number of weights and then must pack our knapsack with the minimum number of weights that will make it a given weight. In general, the problem is:
- Given a set of numbers A and a number b.
- Find a subset of A which sums to b (or gets nearest to it).
So imagine you have a set of weights of 1, 4, 6, 8 and 15, and we want to get a weight of 28, we could thus use 1, 4, 8 and 15 (1+4+8+15=28).
So our code would become 11011 (represented by ‘1’, ‘4’, no ‘6’, ‘8’ and ‘15’).
Then if our plain text is 11011, with a knapsack of 1, 4, 6, 8, 15, we have a cipher text of 1+4+8+15 which gives us 28.
A plain text of 00001 will give us a cipher text of 15.
With public key cryptography, we have two knapsack problems. One of which is easy to solve (private key), and the other difficult (public key).
Creating a public and a private key
We can now create a superincreasing sequence with our weights where the current value is greater than the sum of the preceding ones, such as {1, 2, 4, 9, 20, 38}. Superincreasing sequences make it easy to solve the knapsack problem, where we take the total weight, and compare it with the largest weight, if it is greater than the weight, it is in it, otherwise, it is not.
For example with weights of {1,2,4,9,20,38} with a value of 54, we get:
Check 54 for 38? Yes (smaller than 54). [1] We now have a balance of 16.
Check 16 for 20? No. [0].
Check 16 for 9? Yes. [1]. We now have a balance of 5.
Check 5 for 4? Yes. [1]. We now have a balance of 1.
Check 1 for 2? No. [0].
Check 1 for 1? Yes [1].
Our result is 101101.
If we have a non-superincreasing knapsack such as {1,3,4,6,10,12,41}, and have to make 54, it is much more difficult. So a non-superincreasing knapsack can be the public key, and the superincreasing one is the private key.
Making the Public Key
We first start with our superincreasing sequence, such as {1,2,4,10,20,40} and take the values and multiply by a number n, and take a modulus (m) of a value which is greater than the total (m — such as 120). For n we make sure that there are no common factors with any of the numbers. Let’s select an n value of 53, so we get:
1×53 mod(120) = 53
2×53 mod(120) = 106
4×53 mod(120) = 92
10×53 mod(120) = 50
20×53 mod(120) = 100
40×53 mod(120) = 80
So the public key is: {53,106,92,50,100,80} and the private key is {1, 2, 4, 10, 20,40}. The public key will be difficult to factor while the private key will be easy.
Let’s try to send a message that is in binary code:
111010 101101 111001
We have six weights so we split into three groups of six weights:
111010=53 + 106 + 92 + 100 = 351
101101 = 53+92+50+80 = 275
111001 = 53 + 106 + 92 + 80 = 331
Our cipher text is thus 351 275 331.
The two numbers known by the receiver is thus 120 (m — modulus) and 53 (n multiplier).
We need n^(−1), which is a multiplicative inverse of n mod m, i.e. n(n−1) = 1 mod m. For this we find the inverse of n (_n):
_n = 53^(-1) mod 120
(53 x _n) mod 120 = 1
So we try values of _n in (53 x _n mod 120) in order to get a result of 1:
So the inverse is 77 [Calculator].
The coded message is 351 275 331 and is now easy to calculate the plain text:
351×77 mod(120) = 27 = 111010 (1+2+4+20)
275×77 mod(120) = 55 = 101101
331×77 mod(120) = 47 = 111001
The decoded message is thus:
111010 101101 110001
which is the same as our original message:
111010 101101 111001
The decoding was so easy, the only thing we had was to find the inverse which is not too difficult.
Try this example here.
On this Wiki page [Here], the private key is {2, 7, 11, 21, 42, 89, 180, 354}, n=792, m=881, with data of “01100001” which gives a public key of {295, 592, 301, 14, 28, 353, 120, 236} and gives a cipher of “1129”. Try example here.
So, now let’s look at an improved method, and which has not been cracked …
Naccache-Stern Knapsack Cryptosystem
Initially, we select a large prime number (p). We then select a value (n) and for i from 0 to n, we select the first n prime numbers (p_0…p_{n−1} of which p_0 is 2. We must make sure that:
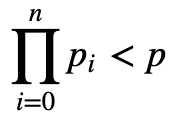
For our secret key (s) we make sure that:

and where gcd(a,b) is the greatest common denominator between a and b. We can implement this in Python with:
s= random.randint(0, p-1)
while (libnum.gcd(p-1,s)!=1):
s=(s+1)%pTo compute the public key (v_i), we calculate:

We can implement this with:
def findnroot(b,k,p):
(m,s,v) = xgcd(k,p-1)
if (v==1):
return(pow(b,m,p))To cipher, we take a message of m and then determine the message bits of m_i. We can then cipher with the public key:

This can be implemented with:
for i in range(0,len(m)):
c=(c*pow(v[i],m[i],p)) % pWe then to decrypt:

This can be implemented as:
val=0
for i in range(0,len(m)):
val=val+( (pow(2,i,p)*libnum.invmod(pval[i]-1,p)) ) * (libnum.gcd(pval[i],pow(c,s,p))-1)Some simple code to implement this is [here]:
import random
from libnum import xgcd, gcd, invmod
import sys
def findnroot(b,k,p):
(m,s,v) = xgcd(k,p-1)
if (v==1):
return(pow(b,m,p))
p=2**17-1
v=[0,0,0,0,0,0,0,0]
pval=[2,3,5,7,11,13,17,19]
msg=47
if (len(sys.argv)>1):
msg=int(sys.argv[1])
if (len(sys.argv)>2):
p=int(sys.argv[2])
s= random.randint(0, p-1)
while (gcd(p-1,s)!=1):
s=(s+1)%p
print (f'Message: {msg}')
print (f'\nSecret key: {s}')
for i in range(0,len(pval)):
v[i]=findnroot(pval[i],s,p)
print ("Public Key (V)=",v)
c=1
m = [int(i) for i in bin(msg)[2:]]
m.reverse()
print ("\nMessage bits: ",m)
for i in range(0,len(m)):
c=(c*pow(v[i],m[i],p)) % p
print (f"\nCipher: {c}")
val=0
for i in range(0,len(m)):
val=val+( (pow(2,i,p)*invmod(pval[i]-1,p)) ) * (gcd(pval[i],pow(c,s,p))-1)
print (f"\nDecrypted message : {val % p}")and a sample run [here]:
Message: 11
Secret: 35786310889612290339071763330496397580015913349470416321791509483080368882165
V= [21627346444663912505779615904445016330005231458433394536621091273384590207012, 6299451311024534885847380345672708184648949045126893280133765118687566924781, 14300133871601848174129793796847602524919769262191112977104332600019586422934, 42978269679178788808917229114117578649372977762512498259297547036020096154849, 15559618002812760554544143149127091153557265669969666082589783466839052376977, 46964097902550262040223237797354828609414770741060683816651606736038381070788, 643540646165740939901790852119372199909483449568447316836290628386972427600, 3148014333594199515748887257879325489173152709940604921416058893233646957089]
Message bits: [1, 1, 0, 1]
Cipher: 6229332976603769302754696916238426220944241155304471731127007212265917007888
Decrypted message : 11Conclusion
And so Shamir cracked the Merkle knapsack public key method, but Naccache and Stern produced a knapsack version that has not yet been cracked. But, it doesn’t have a proof of security, so it has not been adopted that much. If you are a researcher, please consider the method, as some papers are still using it:
- Brier, É., Géraud, R., & Naccache, D. (2017, June). Exploring Naccache-Stern Knapsack Encryption. In International Conference for Information Technology and Communications (pp. 67–82). Springer, Cham.
- Micheli, G., Rosenthal, J., & Schnyder, R. (2016). An information rate improvement for a polynomial variant of the Naccache-Stern knapsack cryptosystem. In Physical and Data-Link Security Techniques for Future Communication Systems (pp. 173–180). Springer, Cham.
- Budiman, M. A., & Sitepu, R. (2018, March). File text security using hybrid cryptosystem with playfair cipher algorithm and Knapsack Naccache-Stern algorithm. In Journal of Physics: Conference Series (Vol. 978, №1, p. 012114). IOP Publishing.
Try it here:
https://asecuritysite.com/principles_pub/knap2
References
[1] Naccache, D., & Stern, J. (1997, May). A new public-key cryptosystem. In International Conference on the Theory and Applications of Cryptographic Techniques (pp. 27–36). Springer, Berlin, Heidelberg.

[2] Merkle, Ralph; Hellman, Martin (1978). “Hiding information and signatures in trapdoor knapsacks”. Information Theory, IEEE Transactions on 24 (5): 525–530. doi:10.1109/TIT.1978.1055927.
[3] Shamir, Adi (1984). “A polynomial-time algorithm for breaking the basic Merkle — Hellman cryptosystem”. Information Theory, IEEE Transactions on 30 (5): 699–704. doi:10.1109/SFCS.1982.5.