Goodbye S3 Bucket Breaches And Hello To Encryption By Default

Goodbye S3 Bucket Breaches And Hello To Encryption By Default
S3 buckets (Amazon Simple Storage Service) are great. They have no structure, and where we can store data objects. Along with this, they are relatively cheap places to store data, and, in the past, have been easy to quickly share files.
We can replicate S3 buckets over different geographical regions and can apply an access policy on buckets. They also allow public access to data and can be encrypted on the server. S3 storage costs $0.023 per GB for the first 50TB. Thus a 1TB data storage will cost around $23 per month.
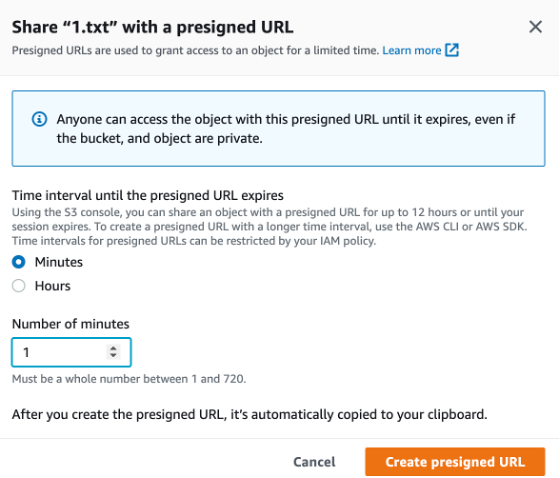
But, they have been responsible for so many data breaches, and where databases have been stored within the buckets and then discovered by others. And so things are changing as AWS now forces sharing to happen only a short time period (Figure 1).
But the major change is that AWS will encrypt data objects put in the buckets, by default. AWS see security as one of the key features in their infrastructure and the move to encryption by default in the S3 buckets is a natural move. When an object is put into the bucket, a unique key is created and used to encrypt the data. This encryption key is then encrypted with a root key — known and envelope encryption.
For the encryption, we can either use Amazon-managed keys (SSE-S3), or can use the AWS Key Management Service (SSS-KMS). With KMS, the administrator can create their own keys which Amazon cannot access to the root key, while SSE-S3 is managed by Amazon (Figure 2).

Encrypting the buckets
If you are worried about files being accessed on the server, it is possible to apply simple encryption to a folder or a set of files. First, select the files and folders that you want to encryption for server-side encryption (Figure 3).

Next, enable server-side encryption, and use an Amazon S3 encryption key. This key will be stored within AWS (Figure 4). After we encryption, we should get a verification (Figure 5).


Encrypting folders and files with KMS
With KMS (Key Manage Service) we can create an encryption key and then encrypt the S3 folder or files. First, go to KMS (Key Management Service), and create a key (Figure 6).

Next, we will create an AES key that will be used for encryption and decryption (Figure 7).

Give the key a name and a description (Figure 8). In this case, name the key “MyKeyBucket”.

We can then define both the administrative permissions (Figure 9) and the usage permissions (Figure 10) on the key. In this case, we will select all of the permissions (but in real life we would lock down the usage of the key).


Finally, we create our key (Figure 11).
Now go back to S3, and select the 1.txt file, and select Server-side encryption. Next select “AWS Management Service Key” (Figure 12), and select the ARN of the key that you have just created.

Conclusions
The cloud can be just as secure as an on-premise system — in fact, even more so. The power of the KMS allows organisations to organise their encryption keys in a secure manner.
If you are interested, we are now running AWS Academy courses, so contact us for more information.