The Strange Tale of the Disappearing Salt … Meet OpenSSL

The Strange Tale of the Disappearing Salt … Meet OpenSSL
Wouldn’t it be annoying if you did a calculation on your calculator and got a certain answer, and then someone with a different calculator go a different answer? Well, that’s what has happened with OpenSSL.
So with OpenSSL, you can’t live with it, and you can’t live without it. For Cybersecurity, OpenSSL is the Swiss Army Knife that both annoy but it is the foundation that we often build on. In fact, OpenSSL nearly brought down the Internet with Heartbleed and has caused a few problems with zero-day threats over the years.
It’s a strange program and stuck at Version 1 for decades, and then, all of a sudden jumped to Version 3. And a little annoying thing in Version 3, is that they changed the way they did symmetric key encryption. With Version 1.x, we can cipher in Linux or Windows with [here]:
Linux command: echo -n "Hello" | openssl enc -aes-128-cbc -pass pass:"qwerty" -e -base64 -S 241fa86763b85341
Windows command: echo | set /p = "Hello" | openssl enc -aes-128-cbc -pass pass:"qwerty" -e -base64 -S 241fa86763b85341
OpenSSL 1.1.1f 31 Mar 2020
Message: Hello
Mode: aes-128-cbc
Password: qwerty
Salt: 241fa86763b85341
========
U2FsdGVkX18kH6hnY7hTQfdhmyrMIw+cu61C/B89/Ek=We can see the cipher is:
U2FsdGVkX18kH6hnY7hTQfdhmyrMIw+cu61C/B89/Ek=If we convert this to binary we see:

The cipher thus starts with “Salted__”. In hex, we see the salt value:
53616C7465645F5F 241FA86763B85341 F7619B2ACC230F9CBBAD42FC1F3DFC49But in OpenSSL 3.x, we get [here]:
Linux command: echo -n "Hello" | openssl enc -aes-128-cbc -pass pass:"qwerty" -e -base64 -S 241fa86763b85341
Windows command: echo | set /p = "Hello" | openssl enc -aes-128-cbc -pass pass:"qwerty" -e -base64 -S 241fa86763b85341
OpenSSL 3.0.0 7 sep 2021 (Library: OpenSSL 3.0.0 7 sep 2021)
Message: Hello
Mode: aes-128-cbc
Password: qwerty
Salt: 241fa86763b85341
========
92GbKswjD5y7rUL8Hz38SQ==This time there is no “Salted__” string:
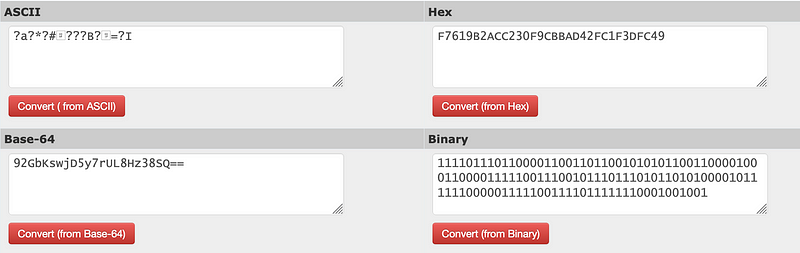
As we can see, the cipher is exactly the same:
F7619B2ACC230F9CBBAD42FC1F3DFC49
But the salt value is missing. And, so, if you want to transmit this cipher, you will have to manually add your salt value to it. If you just send the cipher, there is very little chance you will be able to decrypt it, and thus need the salt value, too. Doh!
You can learn a whole lot about OpenSSL here: