Beware of an Ransomware Attack on ESXi Servers
Beware of the Latest Ransomware Attack on ESXi Servers
A vulnerability - tracked as CVE-2021–21974 — on the OpenSLP service is being used to attack unpatched VMWare ESXi servers. At the current time there are hundreds of servers affect, and where France seems to be particularly badly affected.
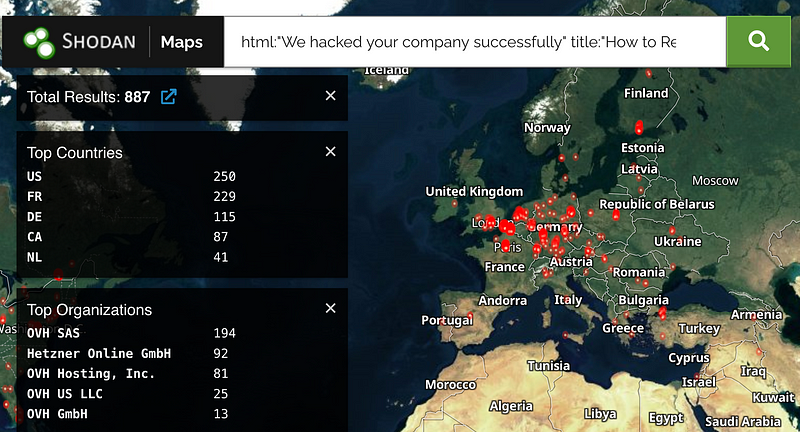
If you use Shodan, then try ‘html:”We hacked your company successfully” title:”How to Restore Your Files”’ and we get a map of affected systems (many in France, for some reason) [here]:
Search query: html:"We hacked your company successfully" title:"How to Restore Your Files"www.shodan.io

And a search gives around 896 servers affected over the world, with 232 in France (of which 197 relate to the OVH SAS organisation), and 115 in Germany (many related to the Hetzner Online GmbH organisation):

As we can see, OVHcloud — a French cloud provider —has been particularly badly affected. The infected server then shows the ransomware message of:

2 Bitcoins (around $40K) is asked as a ransom request.
Conclusions
Make sure you have a fully patched for the VMWare ESXi infrastructure. The compromised systems focus on ESXi Version 6.x and ESXi hypervisor version before 6.7. And for those who run Cloud-based systems? They must patch them, otherwise customer’s data could be lost.