Privacy, Integrity and Trust: Some Day We Will Integrate These Into All Our Communications — The…

Privacy, Integrity and Trust: Some Day We Will Integrate These Into All Our Communications — The Mighty GPG
When was the last time you received an email, and could tell if you definitely knew who sent it, you knew no one else could have read it, and that someone might has not changed something in the message? Well, almost never! Why? Because email is such a poor communication channel for its privacy, integrity and trustworthiness, but still we blindly use it. And for cybersecurity attack vectors, email is still the top threat.
Is there a better way? Well, yes!
If you are dealing with sensitive and/or classified information, you should be using encrypted communications. For this, Bob basically needs the public key of Alice, and add it to his digital key ring. Bob then uses Alice’s public key to encrypt a random symmetric key that he generates. The only key that can reveal the random symmetric key is the private key of Alice:
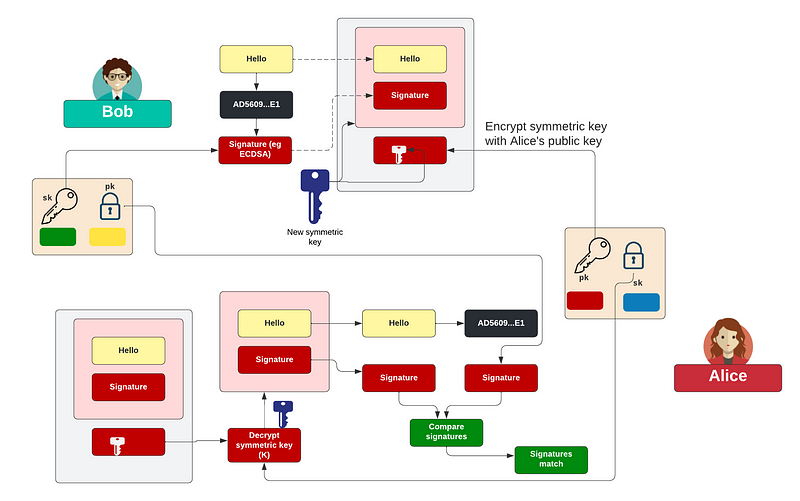
A great advantage of this approach is that Bob can sign a hash of the message with his private key, and then Alice can check this with his public key. We now have privacy (with the symmetric key), integrity (with the hashing of the message and the checking of the signed hash), and trust (with the checking of the signed hashed and proof that it was Bob who sent it).
Meet GPG
It was Phil Zimmerman who created the PGP (Pretty Good Privacy), and which has advanced to the GNU Privacy Guard (GPG). Overall GPG is a program that is based on OpenPGP and can generate keys pairs, encrypt and decrypt data, and digitally sign files and verify digital signatures. This page uses Version 2.4.0. It supports the public key methods of RSA, ELG, DSA, ECDH, ECDSA, and EDDSA. Also symmetric key ciphers of IDEA, 3DES, CAST5, BLOWFISH, AES, AES192, AES256, TWOFISH, CAMELLIA128, CAMELLIA192, and CAMELLIA256, along with SHA1, RIPEMD160, SHA256, SHA384, SHA512, and SHA224. The compression methods supported are ZIP, ZLIB, and BZIP2.
For this we can install GPG [here], and which should install an executable (and a standalone version of GPG). If possible, GPG Version 2 is the best, as it supports a range of elliptic curve signatures, including ECDSA and EdDSA. Next we can link to the executable with Python GnuPG [here].
To create a key pair, we need: the type (RSA, ECDSA or EdDSA), the user name, their email address, and a passphrase. If we have an RSA key pair, we define the size of the keys, such as for RSA-1024, RSA-2048, and RSA-4096. If we have ECDSA, we need to define the curve, such as secp256k1 or NIST P256. For EdDSA, we normally define the curve as Curve 25519 (and use Ed25519 for the keys). The following code thus generates a number of key types:
import gnupg
import sys
gpg = gnupg.GPG(gnupghome="c:\\gpg")
enc="rsa-1024"
password="password"
user="Fred Bloggs"
email="[email protected]"
if (len(sys.argv)>1):
enc=str(sys.argv[1])
if (len(sys.argv)>2):
password=str(sys.argv[2])
if (len(sys.argv)>3):
user=str(sys.argv[3])
if (len(sys.argv)>4):
email=str(sys.argv[4])
input_data = gpg.gen_key_input(key_type="RSA",key_length=1024,passphrase=password,name_real=user,name_email=email)
if (enc=="ecdsa-p256"):
input_data = gpg.gen_key_input(key_type="ECDSA",key_curve='nistp256',passphrase=password,name_real=user,name_email=email)
if (enc=="ecdsa-p384"):
input_data = gpg.gen_key_input(key_type="ECDSA",key_curve='nistp384',passphrase=password,name_real=user,name_email=email)
if (enc=="ecdsa-p521"):
input_data = gpg.gen_key_input(key_type="ECDSA",key_curve='nistp521',passphrase=password,name_real=user,name_email=email)
if (enc=="ecdsa-secp256k1"):
input_data = gpg.gen_key_input(key_type="ECDSA",key_curve='secp256k1',passphrase=password,name_real=user,name_email=email)
if (enc=="eddsa"):
input_data = gpg.gen_key_input(key_type="EDDSA",key_curve='ed25519',passphrase=password,name_real=user,name_email=email)
if (enc=="rsa-1024"):
input_data = gpg.gen_key_input(key_type="RSA",key_length=1024,passphrase=password,name_real=user,name_email=email)
if (enc=="rsa-2048"):
input_data = gpg.gen_key_input(key_type="RSA",key_length=2048,passphrase=password,name_real=user,name_email=email)
if (enc=="rsa-3072"):
input_data = gpg.gen_key_input(key_type="RSA",key_length=3072,passphrase=password,name_real=user,name_email=email)
key = gpg.gen_key(input_data)
fp = key.fingerprint
print ("Key ID: ",fp)
print ("Type: ",enc)
ascii_armored_public_keys = gpg.export_keys(fp)
print("Public key:\n",ascii_armored_public_keys.replace(chr(13),''))
ascii_armored_private_keys = gpg.export_keys(fp,True,passphrase=password)
print("Private key:\n",ascii_armored_private_keys.replace(chr(13),''))
print("Private key deleted: ",gpg.delete_keys(fp,True,passphrase=password))
print("Public key deleted: ",gpg.delete_keys(fp))A sample run for RSA-1024 is [here]:
Key ID: E2728597FE4C56AB211B40F9DCDFA59903EB6813
Type: rsa-1024
Public key:
-----BEGIN PGP PUBLIC KEY BLOCK-----
mI0EY+oDWgEEALwMAM1SefOei3tcrzyaxE/ibdfbfcJCo+eA4PwpHOPiiH2mQYyU
mLqBLLt/F+rdDJY4mDKYkmPreObvhGp2meGpUyDf01d9jANQx0EIWDju3KXA9EdE
3Lp+QFhQWSYA/rgIrME2pAShn2bxF2ESM83XYPW30h5D2DRj94OJe7ShABEBAAG0
G0ZyZWQgQmxvZ2dzIDxmcmVkQGhvbWUuY29tPojRBBMBCAA7FiEE4nKFl/5MVqsh
G0D53N+lmQPraBMFAmPqA1oCGy8FCwkIBwICIgIGFQoJCAsCBBYCAwECHgcCF4AA
CgkQ3N+lmQPraBOnrAP/c1NDE4OTPRJp8SkRUPMwQjStu/jnJ6fEM5NoyDy1iQPJ
wxW7YkLPvAPhbPoExWhIenKeqeH8PaVdqSCt7tr04WjamQiGf66OVqjetPb3hOqv
S/eScHlg9qd68SxIhVoPNWb/Zzt7E94QNS3ZZsleyTj09HrlKKM5DbjJoW9oxdI=
=IiJW
-----END PGP PUBLIC KEY BLOCK-----
Private key:
-----BEGIN PGP PRIVATE KEY BLOCK-----
lQIGBGPqA1oBBAC8DADNUnnznot7XK88msRP4m3X233CQqPngOD8KRzj4oh9pkGM
lJi6gSy7fxfq3QyWOJgymJJj63jm74RqdpnhqVMg39NXfYwDUMdBCFg47tylwPRH
RNy6fkBYUFkmAP64CKzBNqQEoZ9m8RdhEjPN12D1t9IeQ9g0Y/eDiXu0oQARAQAB
/gcDAglYHcBL14Lgygpw6MCoYwGazwihMaRjG/brI9EC7iiJTZJXCn4o3OqPdHN+
9fyUziDyXN0DtEZoGK2s9PRtbeH8Rg7Wbd7Cry5FFlUdlkUTZdEVKdbgDT0ROe0I
4ohWn+B423+rDDtY+MD1qyegalLMXuDhsGnZrg73zfFwOOjkmsrImU2B3rC4XQBp
vCfIfFUub8oNw9cTnmsNUAGjWZ3tkMoYlRTq6c5vNdn4TvW7Vb9eegDKu2hSTGFL
/ORn9NknTzs/HavhZN/61bryZQCGXdLfeXtg+dMfu8AHEUCuCDoz+C/79RGatqyS
O9d9vZ3AO/JsbMegiURK1DY+gVAfVnPRTJCBipo0wnJ5XjejZijw3VGxtmt87A5i
0UzUzh7kO2xXOV1qXCkYwoSTo53Ognfe+4wgmky6bSfMVXCpsx/dyDPjO4VrZFmQ
uV8H7fJp4R8BACINj16lzPn/bbFQCgWYbmjUivio7KhNCiJABvDp+S60G0ZyZWQg
QmxvZ2dzIDxmcmVkQGhvbWUuY29tPojRBBMBCAA7FiEE4nKFl/5MVqshG0D53N+l
mQPraBMFAmPqA1oCGy8FCwkIBwICIgIGFQoJCAsCBBYCAwECHgcCF4AACgkQ3N+l
mQPraBOnrAP/c1NDE4OTPRJp8SkRUPMwQjStu/jnJ6fEM5NoyDy1iQPJwxW7YkLP
vAPhbPoExWhIenKeqeH8PaVdqSCt7tr04WjamQiGf66OVqjetPb3hOqvS/eScHlg
9qd68SxIhVoPNWb/Zzt7E94QNS3ZZsleyTj09HrlKKM5DbjJoW9oxdI=
=XA59
-----END PGP PRIVATE KEY BLOCK-----If I now try this public key [here], I get:

For RSA-2048, we have larger keys, and where the RSA modulus is 2,048 bits long [here]:
Key ID: 3F3151C450A6075E643D1AA32D3C1A6A46928499
Type: rsa-2048
Public key:
-----BEGIN PGP PUBLIC KEY BLOCK-----
mQENBGPqBQQBCACpEKQ6DUn7FOTDB203cPBX5PCodxQ37x9la5ich0yoKtU71l9U
mpwuncTZaFrtNsML7xUuC5WvMvclgX5ELCkMuX+mdvi/rMBQBMrbuYKw/3+/IhjJ
JBwMmJVRI6f2oQrlHYeJEE2m0oyUyiMaWiKoi8xMmik1UGCOh22taKrcMXqwkdO2
UO42na6b0GaswHcToGaC0ZA53Rh80sjP6lMEJbxMd8gB4jf8Q0PXQKtmANKA9hMv
8rPiCuA97p4sCkFRaKoIH6Yaiz2ePC1KoqAmn0be50e4ruaBh8R6EOIOnG0h8WdN
GpT/IbLLBhphFRyZV9R+k+oNEmRGWYYcmuuTABEBAAG0G0ZyZWQgQmxvZ2dzIDxm
cmVkQGhvbWUuY29tPokBUQQTAQgAOxYhBD8xUcRQpgdeZD0aoy08GmpGkoSZBQJj
6gUEAhsvBQsJCAcCAiICBhUKCQgLAgQWAgMBAh4HAheAAAoJEC08GmpGkoSZzl4I
AJ8fEhLaEHHYzsq9n3LRK5E1yKL7IM/iuD62viPI0N0LaRiI4rfUTGo7mAHmCFcB
CorMg4ljYHm91ihZWVJwyu9NnIClE/w9yzG6L/7KQWMJOWiPIQl0EZgwWfS1kXWJ
RWQWDhNprW0q7f3/nDx7oVJGszeqrriXSx2HYXC6thnfoS9mqd5c1JJDqw9Ol32g
kae/Sh+wbgr7fd/1R+ygsDlWku34OjR+RupJtpSOh8Qc5ciHBo+w8LWpEmCNXZ7j
1e2BgQz+dGFn7eNonSmDXW4SFF96uTEOqOEePU+r+W9y0QvS2p2MQVAecTsqB0CI
p51RCb/nejyAyOyfkWwczmM=
=o7uF
-----END PGP PUBLIC KEY BLOCK-----
Private key:
-----BEGIN PGP PRIVATE KEY BLOCK-----
lQPGBGPqBQQBCACpEKQ6DUn7FOTDB203cPBX5PCodxQ37x9la5ich0yoKtU71l9U
mpwuncTZaFrtNsML7xUuC5WvMvclgX5ELCkMuX+mdvi/rMBQBMrbuYKw/3+/IhjJ
JBwMmJVRI6f2oQrlHYeJEE2m0oyUyiMaWiKoi8xMmik1UGCOh22taKrcMXqwkdO2
UO42na6b0GaswHcToGaC0ZA53Rh80sjP6lMEJbxMd8gB4jf8Q0PXQKtmANKA9hMv
8rPiCuA97p4sCkFRaKoIH6Yaiz2ePC1KoqAmn0be50e4ruaBh8R6EOIOnG0h8WdN
GpT/IbLLBhphFRyZV9R+k+oNEmRGWYYcmuuTABEBAAH+BwMCAwiurM16QdrKJcl0
TC1KM9CjOBBihFskrAgOyusFewwgjSvULk0Uc5CeT8FnoBYMsn9U0UJZwE2xqlPt
3LYbPSfsY5/jXaglLUZLYSTTYxHOpM6Zs5Cx1FYu7BEhtN4u8/PK0b4NqpjdX7G0
Rxrppgn+L2AU51CLE0B/hkD0obrPhE7k3EfXYqKKd+UfPFChFmi+/pa32PBSN+pB
gfSoFpLY3LQa4E0WEITzivhdWXpooCzvpv5Qz0RyNk9QeJM0YVvWpNyXKjB1heho
r8bev5nkyNiy34lWOE08YNc/v1S6VLJNTdfBMbELKjvG9BIxnFgEbSXHr6Y+M19y
NP9a+95anGmZvDKEz51ZFazH73a5vmDRx0cw35pf0ITWFV4xVnRsH/98WIn8jD9F
Y8CXR7rAECNuCZjIsbNL2aABZsBmBUXnNpfr8Q6kHRdnI7IdrI36yxXD93C45eZy
LHEZZHGkMUx/aq42lk3YHFwkKJyLYDjKkPvQvWX2MpsGsZ8fXGeyBx8IqYcqnPw3
rai1IcEfOJBR/q3rSYNB7QxatBfLmV5KW/+esTRcw451uWLkhr5lND8GPbW+GLYl
wIENK46PJJVQNhBgvkfsVBL5qRc70IXkhykflfD4M5xMxjroiLGnDvhkoQ+r5+dF
p0EDcstIDWc5bbb2epmQWoj23tnegS845kCIgvkiNgtsLdTg2D8AfH1jDT/TqFZI
ybZ19WLHZANTbbEQJ57QVs/koDadNLXtS75tBN5nuZhbrxVz/a6aiAgfBvK0ct1q
PT/O9Sjj4NY0LN7Qs1tbfHruktmTFPruthHnglDS+GhgfhPybNatGxVYqv7lh/KI
xA6XZFW8jBdcmZJeWkQo6gAkoCji/V8IBFfK+aaUMNIPOsLFNURnHqqvxbo2U4QX
uyCeABfDj322tBtGcmVkIEJsb2dncyA8ZnJlZEBob21lLmNvbT6JAVEEEwEIADsW
IQQ/MVHEUKYHXmQ9GqMtPBpqRpKEmQUCY+oFBAIbLwULCQgHAgIiAgYVCgkICwIE
FgIDAQIeBwIXgAAKCRAtPBpqRpKEmc5eCACfHxIS2hBx2M7KvZ9y0SuRNcii+yDP
4rg+tr4jyNDdC2kYiOK31ExqO5gB5ghXAQqKzIOJY2B5vdYoWVlScMrvTZyApRP8
Pcsxui/+ykFjCTlojyEJdBGYMFn0tZF1iUVkFg4Taa1tKu39/5w8e6FSRrM3qq64
l0sdh2FwurYZ36EvZqneXNSSQ6sPTpd9oJGnv0ofsG4K+33f9UfsoLA5VpLt+Do0
fkbqSbaUjofEHOXIhwaPsPC1qRJgjV2e49XtgYEM/nRhZ+3jaJ0pg11uEhRferkx
DqjhHj1Pq/lvctEL0tqdjEFQHnE7KgdAiKedUQm/53o8gMjsn5FsHM5j
=xPNy
-----END PGP PRIVATE KEY BLOCK-----Again, if we paste the public key [here], we get:

For ECDSA with NIST P-256, we can see shorted keys, as we only need a 256-bit private key and a 512-bit public key [here]:
-----BEGIN PGP PUBLIC KEY BLOCK-----
mFIEY+laIBMIKoZIzj0DAQcCAwQyqwvyzudbI/SasQPfwk8wTKTpfGS943Pfpocq
X6WNlUr79fm3YriOgBLNbWl92fiQ04jrVLuO4qFHjXRXCqY3tBtGcmVkIEJsb2dn
cyA8ZnJlZEBob21lLmNvbT6IkwQTEwgAOxYhBCgJu09BnND1s5jVBNE2PiMXDdki
BQJj6VogAhsjBQsJCAcCAiICBhUKCQgLAgQWAgMBAh4HAheAAAoJENE2PiMXDdki
vQEBAMLDBI7lPPbNFl2bBr37qdzMD8MWcFI1x+VWonJAWmzfAQDgQX7BNz2C4ql0
AtaLG+LfbW8KPTsVIVcwOBkJVTC/gw==
=Y0Y+
-----END PGP PUBLIC KEY BLOCK-----
Private key:
-----BEGIN PGP PRIVATE KEY BLOCK-----
lKUEY+laIBMIKoZIzj0DAQcCAwQyqwvyzudbI/SasQPfwk8wTKTpfGS943Pfpocq
X6WNlUr79fm3YriOgBLNbWl92fiQ04jrVLuO4qFHjXRXCqY3/gcDAr29l+/OcJdm
ymBkFTA6Li1y0GOLtkhWP30/F5LvyLlER9OXplzcs7j0oBJ+ZN9rRRC6W97sy4tj
/s2YBr8JZTKUT+V0TWJXTpGmepbqL+G0G0ZyZWQgQmxvZ2dzIDxmcmVkQGhvbWUu
Y29tPoiTBBMTCAA7FiEEKAm7T0Gc0PWzmNUE0TY+IxcN2SIFAmPpWiACGyMFCwkI
BwICIgIGFQoJCAsCBBYCAwECHgcCF4AACgkQ0TY+IxcN2SK9AQEAwsMEjuU89s0W
XZsGvfup3MwPwxZwUjXH5VaickBabN8BAOBBfsE3PYLiqXQC1osb4t9tbwo9OxUh
VzA4GQlVML+D
=KamW
-----END PGP PRIVATE KEY BLOCK-----and for NIST P-521 the key sizes are larger (521 bits for the private key) [here]:
Key ID: C2E0A8F95633536EB7D05F4C37D7097A6371A8BE
Type: ecdsa-p521
Public key:
-----BEGIN PGP PUBLIC KEY BLOCK-----
mJMEY+laNxMFK4EEACMEIwQA8A0Kz1i/3baTHi1M37Qj3o60CdT6eXRyGHr72VYn
42NpsPEfbXhF+dUkGKXwonFMrSpr3dJDeoLMEPqr4GludYIAvIpPWopkPbEkyUB7
FSGQ9bpfHuqDy0L5RGE4k6dDkpEVmb7jl9CHvKYomU2doAFcmr2LQlT/NpHsiA+v
i/f/1Zq0G0ZyZWQgQmxvZ2dzIDxmcmVkQGhvbWUuY29tPojXBBMTCgA7FiEEwuCo
+VYzU2630F9MN9cJemNxqL4FAmPpWjcCGyMFCwkIBwICIgIGFQoJCAsCBBYCAwEC
HgcCF4AACgkQN9cJemNxqL7enAIJAf4WHrAwGeoRkUKwohIbplFORfad/HZDZH7G
fDxnqKeVLpHtMgSKlX5jhKdNJZwWvgy9BASSsyB+SFyLCLhBj3DoAgkBWnZryEqN
XrFGWUFr41HMLEKxXDfEUSieeTCRNkS8zODOWcemdzEc6em/1sqoySP2dmT8NRFx
BqaRoyl9MRmyp3c=
=gUWO
-----END PGP PUBLIC KEY BLOCK-----
Private key:
-----BEGIN PGP PRIVATE KEY BLOCK-----
lQEHBGPpWjcTBSuBBAAjBCMEAPANCs9Yv922kx4tTN+0I96OtAnU+nl0chh6+9lW
J+NjabDxH214RfnVJBil8KJxTK0qa93SQ3qCzBD6q+BpbnWCALyKT1qKZD2xJMlA
exUhkPW6Xx7qg8tC+URhOJOnQ5KRFZm+45fQh7ymKJlNnaABXJq9i0JU/zaR7IgP
r4v3/9Wa/gcDAg3buJmP0QDRyvMGlsik5lqJ7A5UP1HCf8ft5Ngcg2bU60t0WeEy
wTfj6uoV/2c4BBuCh++JQMBOMULHTpDo64LRLqqDz+hXEvfHiejqDek7MBLXz2ZA
m7ot6akzcGaaMT/U/2xHzJ/eXTEmY3FTdS+0G0ZyZWQgQmxvZ2dzIDxmcmVkQGhv
bWUuY29tPojXBBMTCgA7FiEEwuCo+VYzU2630F9MN9cJemNxqL4FAmPpWjcCGyMF
CwkIBwICIgIGFQoJCAsCBBYCAwECHgcCF4AACgkQN9cJemNxqL7enAIJAf4WHrAw
GeoRkUKwohIbplFORfad/HZDZH7GfDxnqKeVLpHtMgSKlX5jhKdNJZwWvgy9BASS
syB+SFyLCLhBj3DoAgkBWnZryEqNXrFGWUFr41HMLEKxXDfEUSieeTCRNkS8zODO
WcemdzEc6em/1sqoySP2dmT8NRFxBqaRoyl9MRmyp3c=
=Zubb
-----END PGP PRIVATE KEY BLOCK-----Overall, ECDSA and EdDSA are used for digital signing, but where RSA can be used for encryption and digital signing. RSA, though, does have larger key sizes.
Conclusions
In many ways, the Internet has never really grown up since the 1980s, and the protocols we use are still much the same as they were then. But, our world has changed, so go and some keys and do cybersecurity properly: