Single-Tenant or Multi-Tenant HSMs? Do You Trust Your Cloud Provider Not To Peek At Your Keys?

Single-Tenant or Multi-Tenant HSMs? Do You Trust Your Cloud Provider Not To Peek At Your Keys?
Your encryption keys are your crown jewels. Lose or compromise them, and you are likely to have significant costs. In fact, a breach of a trust infrastructure has been assessed as the most costly of all cybersecurity attacks.
And, so, we are increasingly moving our data infrastructures from on-premise to the public key. So where should we store our encryption keys? Well, it all depends on which level of FIPS 140–2 you need to comply with.
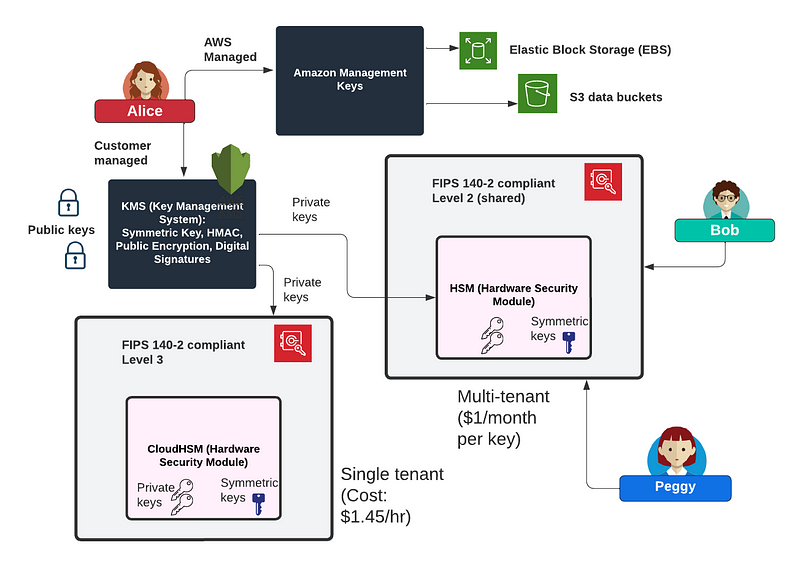
For AWS, we can use an HSM (Hardware Security Module) to store our private and symmetric keys, but this is a multi-tenant system, and where you share the HSM with others. There should be no way that other AWS customers can have access to your keys, but there is the opportunity for AWS to access them. This is FIPS 140–2 Level 2.
For FIPS 140–2 Level 3, we have separation from other users and from AWS, and where we run a CloudHSM. This is much more costly and starts at around $1.45/hr to run in AWS (as compared to around $1/month for using a key in the HSM).
FIPS 140 levels
In 2019, FIPS 140–3 replaced FIPS 140–2. It defines 11 areas of design involved in designing and implementing modules [here][docs]. This includes four security levels for the cryptographic module specification; cryptographic module interfaces; roles, services, and authentication; software/firmware security; operating environment; physical security; non-invasive security; sensitive security parameter management; self-tests; life-cycle assurance; and mitigation of other attacks. Each layer builds on the previous level, and where Level 1 is the lowest level, and Level 4 provides the highest level. For those working in finance and in high-risk areas, Level 3 is often the benchmark, while in defence-related areas, Level 4 would often be applied. Table 1 outlines the differences between the levels.

Physical security
For physical security, the tamper-proof nature of the target system is key, and where tamper detection becomes important at the higher levels of security.

Security levels
As Figure 1 illustrates, Level 1 provides a minimum security level, while Level 2 implements methods around role-based authentication, and also integrates physical tamper evidence. As we move up to Level 3, we integrate identity-based authentication and also have an isolation barrier between the identity system and the place where the keys are stored. This would integrate a secure enclave (such as with the Apple T2 chip), or a hardware security module (HSM).
For Level 4, we see formal models, detailed explanations, and pre/post conditions. It also contains a great integration of tamper detection, with EFP (Environmental Failure Protection) and EFT (Environmental Failure Testing). This would involve testing where other components around the target system were to fail, and for the target to not be compromised. A typical focus is around side channels, such as for radio frequency (RF) or electromagnetic (EM) radiation from devices.

Isolation
For isolation, a method often used is key wrapping, and where a key is protected outside a trusted environment. Within the Cloud, AWS CloudHSM (hardware security module) supports AES key wrapping with the default initialization vector — 0xA6A6A6A6A6A6A6A6- or a user-defined value. This provides a FIPS 140–2 Level 3 environment and where the keys in their raw form are only handled within a trusted cloud instance. The wrapped keys can then exist outside this but only be converted into their actual form within the CloudHSM. A key generated within the CloudHSM can then be wrapped for export from the environment, or imported from an external wrapped key. The AWS CLI is on the form which defines a key handle (with -k) and the wrapping key handle (with -w):
> wrapKey -k 7 -w 14 -out mykey.key -m 5Key Wrapped.
Wrapped Key written to file "mykey.key: length 612
Cfm2WrapKey returned: 0x00 : HSM Return: SUCCESSConclusions
And, so, you need to decide whether you want to share your HSM with others, or run your own. Basically, it typically comes down to the level of FIP 140–2 we want to comply with. Level 3 is much better than Level 2, but you might struggle a bit in getting all our Cloud services to integrate with it, so often it is a balance between the two.