GitHub Says “Ooops!”
GitHub Says “Ooops!”
The Most Costly of Cybersecurity Risks … The Breach of the Private Key: If GitHub can make a mistake, then so can you…
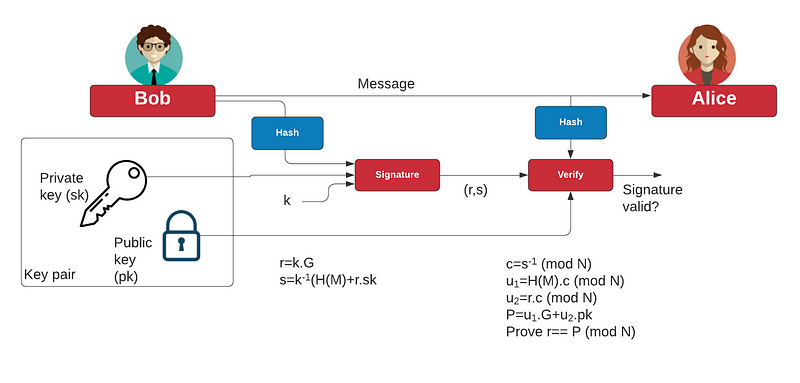
The core trust of our Internet comes down to the usage of private keys. These magical keys are used with an associated public key, and then prove identity by creating a digital signature. Thus when someone logs onto a system, they can register their public key, and where a private key signs the hash of a message. This is then proven with the associated public key. Two of the most popular signature methods are RSA and ECDSA (Figure 1).
And, so, the private key must be guarded, as a breach of this would cause everything that had been digitally signed with it, to be untrusted. The only way out is to revoke the public key and change it on every system it is used with. This can be a messy (and patch) process — and is often embarrassing, especially for cybersecurity-related companies. Basically, if you can’t handle your own private keys properly, how can you be trusted to handle others?
Now, it has been announced that GitHub posted its own RSA SSH keys in a repository. Overall, if the private keys were to be discovered, it could mean that an intruder could remotely log into their infrastructure in a trusted way. For this, GitHub published its announcement on 24 March [here]:

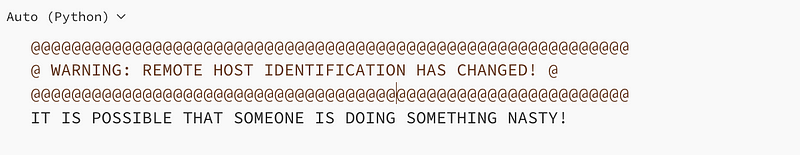
It wasn’t a hacking attempt — just plain old human error. On their system, they received the scary message of:
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY!Luckily, a simple key revocation was all that was required in this case, but companies need to be vigilant about the usage of their private keys, and should certainly be monitoring their usage.
If you want to learn more about digital signatures, try here: