What Have Tweedledee and Tweedledum Got To Do With Cybersecurity?

What Have Tweedledee and Tweedledum Got To Do With Cybersecurity?
And the rhyme goes:
Tweedledum and Tweedledee
Agreed to have a battle;
For Tweedledum said Tweedledee
Had spoiled his nice new rattle.
Just then flew down a monstrous crow,
As black as a tar-barrel;
Which frightened both the heroes so,
They quite forgot their quarrel.So, what have Tweedledum and Tweedlee have to do with cybersecurity? Well, they are the nickname of two elliptic curves that were defined by the zCash team. So, let’s examine them, and see how they differ from two other famous curves: secp256k1 and P256. In fact, the web page you are accessing now is likely to be protected using the ECDH handshake, and it is likely to use the P256 curve. If you are interested, we define this type of curve as a Weierstrass curve.
secp256k1 and P256
And, so, Satoshi Nakamoto selected the secp256k1 curve, and the rest is history. It was a great choice and used the ECDSA signature. With this, we could create a random 256-bit private key, and then take an ECDSA signature from this, and expose it as our public identifier — it was genius!
Basically, secp256k1 uses a 255-bit prime field Weierstrass curve of the form:
y²=x³+7 (mod p)
and where p=2²⁵⁶-2³²-2⁹-2⁸-2⁷-2⁶-2⁴-1. This defines a finite field and gives us 128-bit equivalent security. In Sage, we can code with:
Fq = GF(2^256-2^32-2^9-2^8-2^7-2^6-2^4-1)
secp256k1 = EllipticCurve(Fq, [0, 7])
print ("secp256k1 order: ",secp256k1.count_points())
print ("secp256k1 prime: ",Fq)
Gx= 55066263022277343669578718895168534326250603453777594175500187360389116729240L
Gy= 32670510020758816978083085130507043184471273380659243275938904335757337482424L
G = secp256k1(Fq(Gx), Fq(Gy))
print ("secp256k1 base: ",G)This will determine the number of points in the order, aka the curve order:
secp256k1 order: 115792089237316195423570985008687907852837564279074904382605163141518161494337
secp256k1 prime: Finite Field of size 115792089237316195423570985008687907853269984665640564039457584007908834671663
secp256k1 base: (55066263022277343669578718895168534326250603453777594175500187360389116729240 :
32670510020758816978083085130507043184471273380659243275938904335757337482424 : 1)We can see that the order is less than the prime number. Overall, the order defines the true security of the curves, as that is the number of points we can have. Another popular curve is P256 (secp256r1), and which has the equation of:
y²=-3x³+41058363725152142129326129780047268409114441015993725554835256314039467401291 (mod p)
and where p=2²⁵⁶-2²²⁴+2¹⁹²+2⁹⁶-1. We can code in Sage with:
Fq = GF(2^256-2^224+2^192+2^96-1)
P256 = EllipticCurve(Fq, [-3, 41058363725152142129326129780047268409114441015993725554835256314039467401291])
print ("\nP256 order: ",P256.count_points())
print ("P256 prime: ",Fq)
Gx= 48439561293906451759052585252797914202762949526041747995844080717082404635286
Gy= 36134250956749795798585127919587881956611106672985015071877198253568414405109
G = P256(Fq(Gx), Fq(Gy))
print ("P256 base: ",G)and a run gives:
P256 order: 115792089210356248762697446949407573529996955224135760342422259061068512044369
P256 prime: Finite Field of size 115792089210356248762697446949407573530086143415290314195533631308867097853951
P256 base: (48439561293906451759052585252797914202762949526041747995844080717082404635286 :
36134250956749795798585127919587881956611106672985015071877198253568414405109 : 1)Vesta and Pallas — the Pasta Curves
Two new curves are Vesta and Pallas. These are defined as the Pasta curves and are named after two minor planets in the solar system. It comes from the creators of the highly popular BLS12–381 curve (a pairing-friendly curve which is used in zkSnarks), and which is now used extensively within cryptocurrency applications. The work is included in the zCash Halo 2 project [here] and is based on the Tweedle cycle paper [1]. The base point in both places is the x point which gives a y value of 2:
Fq = GF(2^254 + 45560315531506369815346746415080538113)
Vesta = EllipticCurve(Fq, [0, 5])
print ("\nVesta order: ",Vesta.count_points())
print ("Vesta prime: ",Fq)
Gx= 28948022309329048855892746252171976963363056481941647379679742748393362948096
Gy= 2
G = Vesta (Fq(Gx), Fq(Gy))
print ("Vesta base: ",G)
Fq = GF(2^254 + 45560315531419706090280762371685220353)
Pallas = EllipticCurve(Fq, [0, 5])
print ("\nPallas order: ",Pallas.count_points())
print ("Pallas prime: ",Fq)
Gx=28948022309329048855892746252171976963363056481941560715954676764349967630336
Gy=2
G = Pallas(Fq(Gx), Fq(Gy))
print ("Pallas base: ",G)A sample run of Sage gives:
Vesta order: 28948022309329048855892746252171976963363056481941560715954676764349967630337
Vesta prime: Finite Field of size 28948022309329048855892746252171976963363056481941647379679742748393362948097
Vesta base: (28948022309329048855892746252171976963363056481941647379679742748393362948096
: 2 : 1)
Pallas order: 28948022309329048855892746252171976963363056481941647379679742748393362948097
Pallas prime: Finite Field of size 28948022309329048855892746252171976963363056481941560715954676764349967630337
Pallas base: (28948022309329048855892746252171976963363056481941560715954676764349967630336
: 2 : 1)Tweedledee and Tweedledum
With the Tweedle cycle paper [1], we see the definition of Tweedledee and Tweedledum:

As the paper says, they are attractive because of their security and performance and are defined as:
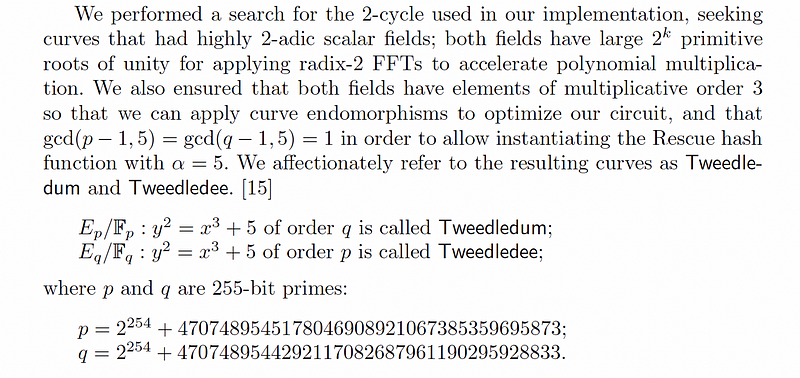
And, so, we have:
y²=x³+5 (mod p)
and where p is 2²⁵⁴ + 4707489545178046908921067385359695873 for Tweedlee, and 2²⁵⁴ + 4707489544292117082687961190295928833 for Tweeledum. Then we can code with Sage using:
Fq = GF(2^254 + 4707489544292117082687961190295928833)
Tweedledum = EllipticCurve(Fq, [0, 5])
print ("\nTweedledum order: ",Tweedledum.count_points())
Gx=28948022309329048855892746252171976963322203655955319056773317069363642105856
Gy=2
G = Tweedledum(Fq(Gx), Fq(Gy))
print ("Tweedledum base: ",G)
Fq = GF(2^254 + 4707489545178046908921067385359695873)
Tweedledee = EllipticCurve(Fq, [0, 5])
print ("\nTweedledee order: ",Tweedledee.count_points())
Gx=28948022309329048855892746252171976963322203655954433126947083963168578338816
Gy=2
G = Tweedledee(Fq(Gx), Fq(Gy))
print ("Tweedledee base: ",G)And where we get:
Tweedledum order: 28948022309329048855892746252171976963363056481941647379679742748393362948097
Tweedledum prime: Finite Field of size 28948022309329048855892746252171976963363056481941560715954676764349967630337
Tweedledum base: (28948022309329048855892746252171976963363056481941560715954676764349967630336
: 2 : 1)
Tweedledee order: 28948022309329048855892746252171976963322203655955319056773317069363642105857
Tweedledee prime: Finite Field of size 28948022309329048855892746252171976963322203655954433126947083963168578338817
Tweedledee base: (28948022309329048855892746252171976963322203655954433126947083963168578338816
: 2 : 1)Conclusions
And, so, that’s what Tweedledee and Tweedledum have to do with Cybersecurity. If you want to see how it is integrated into code, try here: