The Buzz of Real-World Crypto: PQC Goes Into Production
The Buzz of Real-World Crypto: PQC Goes Into Production
Real World Crypto 2023: And “Crypto” means Cryptography!
The problem with academic conferences is often that the papers published can be difficult to read for those who do not have a maths background. This is especially the case for cryptography-related conferences. But, cryptography has had a long track record of “rump sessions”, and which involved practical cracking of cryptography. For this, Len Adleman outlined — in the past — that some of these sessions were often rowdy events:

And, so Real World Crypto is one of the best conferences in breaking down barriers and aims to provide ground-breaking practical research.
At each conference, there is often a great buzz on evolving fields. For Real-World Crypto 2023, there were quite a few presentations on PQC (Post Quantum Cryptography).
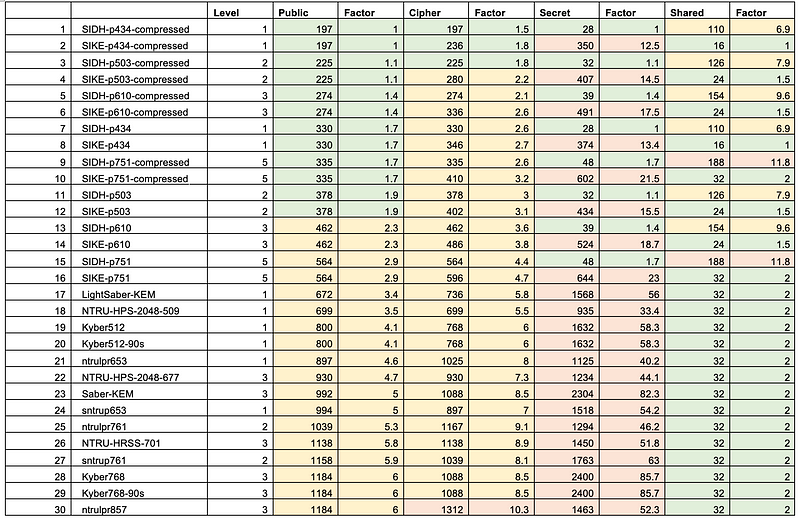
Google has been working on PQC for a TLS method (Application Layer Transport Security — ALTS) to communicate within its own infrastructure. As they started before NIST announced the PQC winners, they selected NTRU-HRSS. Unfortunately, NIST selected CRYSTALS-Kyber for key exchange/public key encryption. As we can see in Figure 2, NTRU (eg NTRU653) requires a public key of 830 bytes, a private key of 1,125 bytes, and ciphertext of 1,025 bytes. As ECC only requires a public key of 64 bytes and a private key of 32 bytes, Google observed that the keys are 9–10 times larger than the existing ECC implementation.
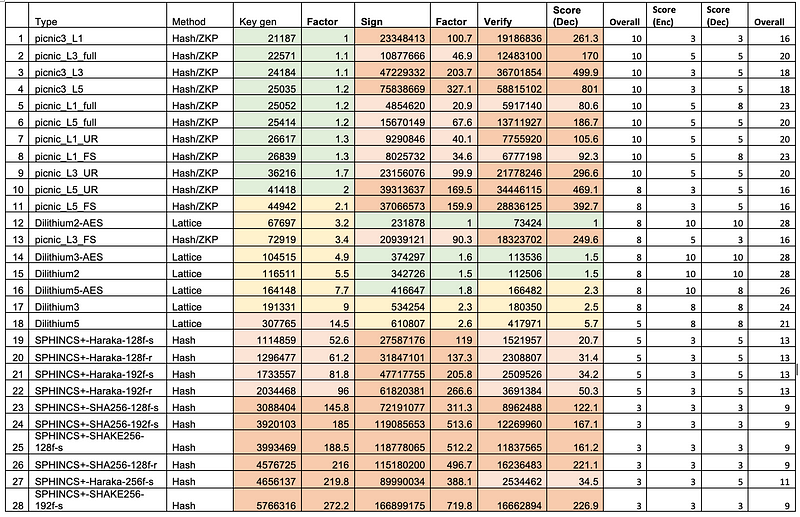
Cloudflare has been working on a PQC implementation of its Privacy Pass system. This identifies users as humans and not bots and uses blinded signatures. For this, they implemented these using the NIST-approved CRYSTALS-Dilithium signature method. The results were positive with around 300ms for proof of signature and around 20 ms for verification, and using 100KB message sizes. This is one of the first applications of a more advanced integration of PQC. As we can see in Figure 3, Dilithium has good performance for signing and verification.
Another company building with Dilithium is NXP [here], and who has been analysing side channel analysis around embedded devices:

They outlined that Kyber had received significant interest for side-channel analysis, but there has not been much work on Dilithium. For this, they have made several advancements in protecting against side channels with Dilithium, especially when using the Keccak hash function. One thing that was highlighted is that the actual implementation of the standard may be difficult because of side-channel issues.
The advancement of PQC is also highlighted with new integrations into existing systems, including with Rosenpass, and which integrates post-quantum cryptography into VPNs using WireGuard [here]:

Conclusions
We are entering a new era … with Post Quantum Cryptography replacing our existing public key methods. I will be one of the most radical changes with the Internet since it was created. So, get involved …