Your LEDs Could Be Leaking Your Encryption Keys!

Your LEDs Could Be Leaking Your Encryption Keys!
Cracking a PQC and an ECDSA Key using Colour
The brute forcing of an encryption key will typically take billions and billions of years to crack. But, if there’s a leakage of some of the information around the key, this could be cut to just minutes. One of the most useful attacks is a side channel attack, which involves some leakage through a secondary channel, such as light, radio waves, or electrical noise. Now, new research has shown that it is possible to recover encryption keys from variations in the intensities of LEDs [here][1]:

The work involved using an iPhone to record the light from an LED, such as one used in a card reader. This involved the ability to derive a 256-bit ECDSA key, and also a SIKE key (used within Post Quantum Cryptography) from a Samsung Galaxy S8 phone. Most work up to this point has used a fairly complex capture and analysis setup, but this work shows that the side channel can be detected purely with the capture from an iPhone:
“One of the most significant things of this paper is the fact that you don’t need to connect the probe, connect a scope, or use a software-defined radio,” — Ben Nassi
Here is an outline of the work:
The SIKE key was captured from the Galaxy device by using the LED on a USB hub which connected audio speakers:

For the recovery of the ECDSA key, the team used a connected CCTV camera, and reading from the LED of a smart card reader. The distance between them was 16 meters:

Overall the colour of the LED changes with changes in the cryptographic key operations:

From analysing colour changes, the research team where able to discover the 0 and 1’s of the key:
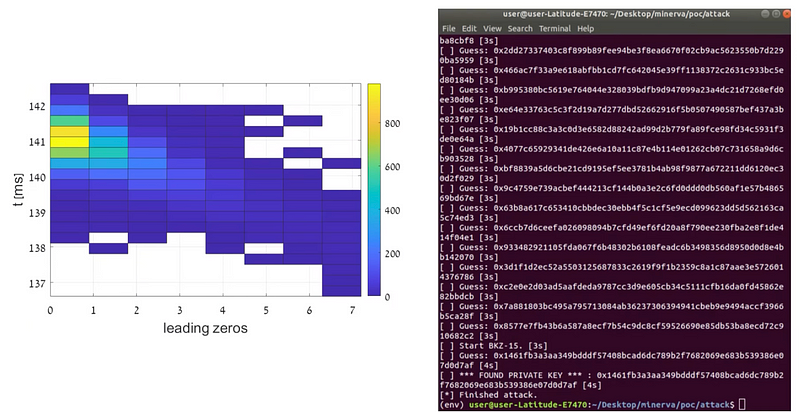
Conclusions
We have done quite a bit of work on RF and electrical noise discovery of keys from a device, and have used an expensive digital oscilloscope to capture signals.

This new work shows that it is possible to perform this analysis on relatively inexpensive equipment. While the attack is practically infeasible in production, it is the start of a new area of investigation into how devices leak information. Here is a live demo that we gave:
Reference
[1] Nassi, B., Iluz, E., Cohen, O., Vayner, O., Nassi, D., Zadov, B., & Elovici, Y. (2023). Video-Based Cryptanalysis: Extracting Cryptographic Keys from Video Footage of a Device’s Power LED. Cryptology ePrint Archive.