Tracking The Identity of Devices By Their Bluetooth Signal Footprint

Tracking The Identity of Devices By Their Bluetooth Signal Footprint
Even though the broadcast address has been randomized
Within BLE (Bluetooth Low Energy), there is a randomization of the address. But this randomness can sometimes be overcome through its usage of counters or from timings. In a new paper, the researchers have broken the address randomization using the Received Signal Strength Indication (RSSI) [here]:

The measurements of RSSI come from the advertising packets from the device and are linked to previous traces to re-identify it. This creates an RSSI fingerprint for the device. For devices which do not move, the research provides a 99% accuracy rate in correctly identifying a device.
In Figure 2, we can see that we monitor the signal strength from a device and where it may be using an address rotation to hide its identity. In this case, the address of AA:AA:AA:AA:AA has been mapped with BB:BB:BB:BB:BB:BB — due to the RSSI monitoring of advertising packets. The measurement of RSSI is in dBm, which is the signal strength in relation to 1mW for power. Overall, -3dB is a drop of one-half, and so, -3dBm is 0.5mW, -6dBm is 0.25mW, and so on. In the figure, we see that AA:…AA has an RSSI of -79dBm and -60dBm, and which is a difference of -19dBm — and where we have around six half power factors. A drop of -3dB thus is a half power drop:
https://asecuritysite.com/wireless/dbm

The team set up a single-receiver experiment, and also multiple receivers. From these experiments, the research team plotted the RSSI for devices and where able to define a basic RSSI fingerprint for the device (Figure 3).

Overall, they used the ROBERT (ROBust and privacy-presERving proximity Tracing) [2] dataset to run their experiments. Overall, ROBERT was used to perform proximity tracing around COVID-19 applications. Figure 4 outlines the data format used, and where the RSSI was mapped from transmitters to receivers and also to the distance between devices. With this, there are also scenarios matched, such as those related to indoor or outdoor measurements.

Overall, a range of Machine Learning (ML) methods. This included HistGradientBoostingClassifier (HGT), RandomForestClassifier
(RF) and KNeighborsClassifier (kNN). For a range of devices (A…O), the paper outlines a strong correlation in matching the devices with a good true positive rate (Figure 5), and where Device A had a 100% success rate of classification for 44 vectors (Figure 6).

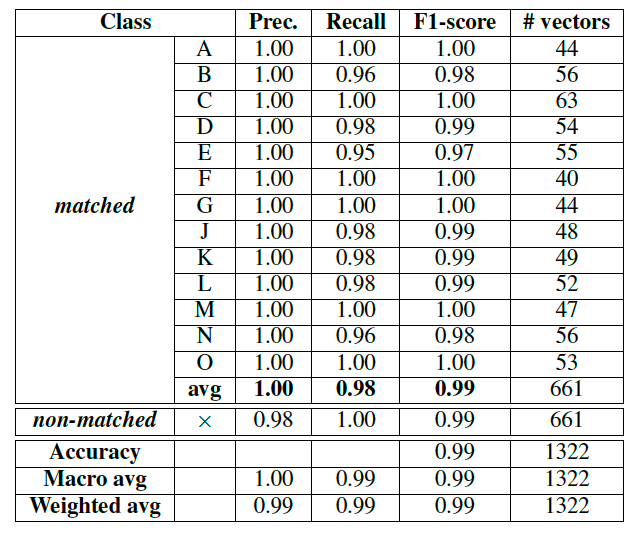
The general accuracy of the ML methods varied with the RSSI, and with HGT less affected by RSSI strength (Figure 7).

Conclusions
The paper shows interesting results, and especially that the HistGradientBoostingClassifier (HGT) method seems to work best for a range of RSSI strengths from the transmitter. If you are interested in learning about dBms, try here:
I love wireless (wi-fi) communications. In fact, I did my PhD around the propagation of radio waves using Maxwell’s…billatnapier.medium.com
References
[1] Guillaume Gagnon, Sébastien Gambs, Mathieu Cunche. RSSI-based Fingerprinting of Bluetooth Low Energy Devices. International Conference on Security and Cryptography (SECRYPT 2023), Jul 2023, Rome, Italy.
[2] Castelluccia, C., Bielova, N., Boutet, A., Cunche, M., Lauradoux, C., Le Métayer, D., & Roca, V. (2020). ROBERT: ROBust and privacy-presERving proximity Tracing.