My Name is Holly, and I Break Into Computers For a Living

My Name is Holly, and I Break Into Computers For a Living
Like a magician with a sleight of hand
I was so privileged to present an endnote talk in Glasgow yesterday on quantum computers: threats and opportunities. But, before my talk, there was a truly excellent presentation by Holly Grace Williams, and whose tagline is “I break into computers for a living”.

The talk was great fun for me, as it is almost like taking a computer back to its historical roots. and where you can lock all the doors of a house but still leave the keys under the mat. Like it or not, Microsoft Windows brings the baggage of several decades with it, and a Windows computer — at its core — is almost like that computer from the original DOS/Windows 3.1 days.
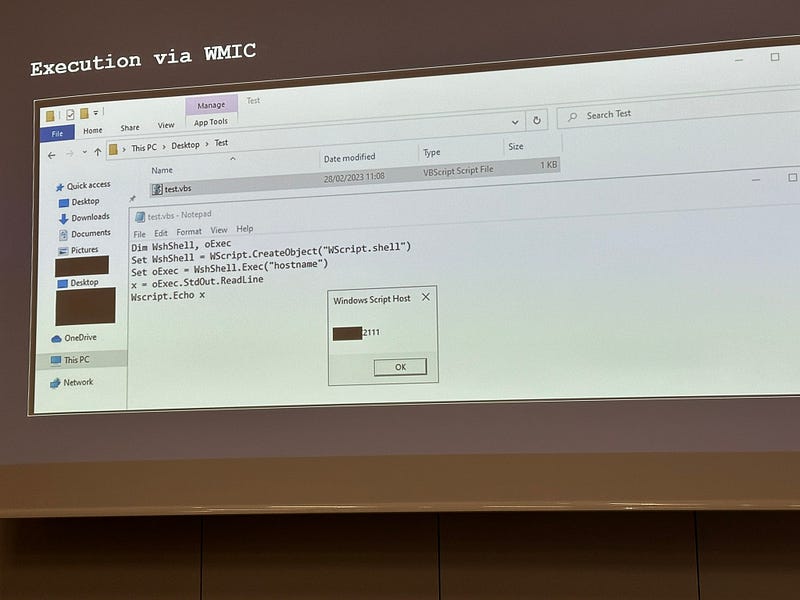
Her scripting can then fall back to either Basic or C# (both are typically supported on Windows systems). And she showed that great testers should have expertience of many programming languages under their belt.
Overall, WMIC provides so much information on a system, and to be able to script with Basic provides a backdoor into a system. And, so she found lots of PDFs which contained possibly sensitive information:

But, how could she get the files off the system, as many applications were closed to her? Well, her trick was to use the mighty certutil program. With certutil, we can create and check digital certificates, and it is a standard part of the Windows system. And, so, Holly grabbed certutil, and ran:

This is such as great hack as it turns a binary format — the PDF — into a text one. In fact, the PDF will then be encoded as a digital certificate (X.509), and which she could then just copy-and-paste the text file off the system — without needing to download Metasploit or Mimikatz. A simple decode was then convert the digital certificate format back into the original PDF format.
Here is an example of what she did:
C:\>dir zkp01.pdf
Volume in drive C has no label.
Volume Serial Number is 06E5-D224
Directory of C:\
08/18/2018 05:59 PM 7,704,572 zkp01.pdf
1 File(s) 7,704,572 bytes
0 Dir(s) 8,960,086,016 bytes free
C:\>certutil -encode zkp01.pdf 111.txt
Input Length = 7704572
Output Length = 10593844
CertUtil: -encode command completed successfully.
C:\>head 111.txt
-----BEGIN CERTIFICATE-----
JVBERi0xLjMKJcTl8uXrp/Og0MTGCjQgMCBvYmoKPDwgL0xlbmd0aCA1IDAgUiAv
RmlsdGVyIC9GbGF0ZURlY29kZSA+PgpzdHJlYW0KeAGVVU1vFDEMvc+vMKWlWWCy
+Z6EI4UDnEAdiQPlgFatBKJAtyD+Ps9Odqb70SI0h2QS289+fklu6D3dkMFXYtFD
ohgMrS/pA32n5dmtpdUtWfluVwfMrmb3ZNi3e9C32nD8KzJ6iK4E6yQsogvc2fm8
0XFa52cU6Q85GtecqHZB7GXinNUl5ES99UUXR6trejmSc1FsnDM65swAWHI6RNuN
17QcR4eKxiv6SOrR0QLeOpB6vEB0S+qYR0fqBBtGF1JPZJJIncokb0w6daFkBU4X
C8wsu03xnm6sn8kEgaatKfRz8fLdHvgmiZ6TQXJ6EwOun2h8S6/Hyvw2H8HrUPko
uatkGG2MSTSuHqKFdmlZGs6MlOWhU+4hVO+8joPnLpT8vy1QfkHj18Pl+IDkdwJL
OcM/ytnrMjpf60mtLjQb1Z0MdVUaQyrX1WZSxMQtOhi2pRd3aWBxGpJTcUiaoehs
C:\>certutil -decode 111.txt a.pdf
Input Length = 10593844
Output Length = 7704572
CertUtil: -decode command completed successfully.
C:\>dir a.pdf
Volume in drive C has no label.
Volume Serial Number is 06E5-D224
Directory of C:\
09/15/2023 02:28 AM 7,704,572 a.pdf
1 File(s) 7,704,572 bytes
0 Dir(s) 8,941,936,640 bytes free
C:\>dir zkp01.pdf
Volume in drive C has no label.
Volume Serial Number is 06E5-D224
Directory of C:\
08/18/2018 05:59 PM 7,704,572 zkp01.pdf
1 File(s) 7,704,572 bytes
0 Dir(s) 8,941,760,512 bytes freeNotice, that we see the standard header for an X.509 certificate:
-----BEGIN CERTIFICATE-----If we look at the tail of the PDF we get:
C:\>tail 111.txt
Njc3ODIwIDAwMDAwIG4gCjAwMDc2NzgwNjUgMDAwMDAgbiAKMDAwNzY5MjIzMCAw
MDAwMCBuIAowMDA3NjkyOTQ2IDAwMDAwIG4gCjAwMDc2OTI1MDAgMDAwMDAgbiAK
MDAwNzY5MjkyNSAwMDAwMCBuIAowMDA3NjkzMTc1IDAwMDAwIG4gCjAwMDc2OTg5
NDMgMDAwMDAgbiAKMDAwNzY5ODk2NSAwMDAwMCBuIAowMDA3Njk4OTkwIDAwMDAw
IG4gCjAwMDc2OTkwNDQgMDAwMDAgbiAKMDAwNzY5OTA3NCAwMDAwMCBuIAowMDA3
Njk5MTE3IDAwMDAwIG4gCjAwMDc2OTkxMzcgMDAwMDAgbiAKdHJhaWxlcgo8PCAv
U2l6ZSAyNTUgL1Jvb3QgMTYzIDAgUiAvSW5mbyAxIDAgUiAvSUQgWyA8ZjZmMDc4
MmFmNmVlZGNiNjM5YzJjNjkwODMxN2IzNDY+CjxmNmYwNzgyYWY2ZWVkY2I2Mzlj
MmM2OTA4MzE3YjM0Nj4gXSA+PgpzdGFydHhyZWYKNzY5OTMwOQolJUVPRgo=
-----END CERTIFICATE-----And when I view the file I have just created, I see that it is back as a PDF file (and with the magic number of ‘%PDF’):
C:\>head a.pdf
%PDF-1.3
%Äåòåëó DÄÆ
4 0 obj
<< /Length 5 0 R /Filter /FlateDecode >>
stream
xUMo1 ½I_0¥¥Y`²ùz,#.o@%å?V-¢@· _>INv▌ûÑ"4╪dUI~~Inè=Y?AWbÑC¢ -/é}åU-¥O-YùnWIrf÷dO·{D·Upü+2z^rë$,¢ ÜUù¼ÑqZçgé9xo"vAìeâoO%äD½oEG«kz9'sQlo3:æI Xr:DU?x'
G╪SÆ+úHêÑÑ_:?z¼@tKê~GGêROd'H?E$oL:u¡dN I,»Mñzn¬YÉ?▌-)ôsñòY
o&%z"ArzrYh|K_ÇEü6 AëPù(1«dmOI4r
¢.viYIO"å¡Sî!Tï¼Zƒç."ü¿-P~AaxAåo?äwK9A?EUë2:_ëI-.4? uUC*xOfRÄÄ-:¥wi`q'SqHs¡èl!Ö_Å?J3:kªW!JO~ 3 E?ªÉ½O^uA<òwºè N,4 nI `;▌Us GEúf9b`éI,
¡ÿe¿?îp+fÜ%;koS÷TVÇÿ-*èê?]7ÑZ«q\,@#²7±sOè"Z%+AéOä7%6OÄsuæEáO`÷ ?ooAç▌
?}Ö>@O]Ö¥NVV1Py12?ºp?z°VG#=gôv ÷Ñ[IgôzA?)_a /MuO^Ü+Va, ;' x6I)XsrôIsgy,FS¬ +I¡"EV=WÄoAdIÇ^-AGí+d%c'ÑaHI'oòô>¼»\_._úyù[·_xÉ'U>YïDW-or-½ú?;O!í?r.-O)bb_q<»?dJLoEOG,x¬-Z
^TA\ënhHE[Z=d]I3-Ö?U`%ån î7êòs].']p LTZ>µEzYûc
²o,·"Ü X!Cƒü lj^ƒ
endstream
endobj
5 0 obj
752and where I can view it:

And, so, we already have Holly signed up to give a talk to our students. Just brilliant. It is great to see people who understand almost every single bit and byte on a computer system and network. For me, I was teleported back to days of playing with Windows scripting and WMIC — and it was so much fun to listen to Holly. I then had to privilege of sharing a panel session with Holly, and where she outlined that it is often the basics that companies forget about and which leaves them vulnerable.
It felt like I had been in the presence of a great magician and who — with a sleight of hand — had performed a great magical trick. Overall, I am a fan of great magicians, and, in this case, most of the audience for Holly’s presentation perhaps didn’t quite see the sleight of hand, but I could see it fully. It was pure magic and showed that even the strongest security can be broken!
And, at the endpoint of her talk, she outlined how the SOC team could see what she had executed; they couldn’t see what she had actually done. So, get your controls in place for your SOC, and be ready for a computer to be stripped back to its core. If Holly is presenting at a venue near you, please go and watch a great magician performing her tricks — and learn from every word she says.
Read more here: