An ASCON Post-Quantum Future?

An ASCON Post-Quantum Future?
And, so, ASCON won the NIST light-weight encryption competition:
https://asecuritysite.com/ascon
ASCON was designed by Christoph Dobraunig, Maria Eichlseder, Florian Mendel and Martin Schläffer from Graz University of Technology, Infineon Technologies, and Radboud University. It is both a lightweight hashing and encryption method. It uses a single lightweight permutation with Sponge-based modes of operation and an SPN (substitution–permutation network) permutation.
Overall, it has an easy method of implementing within hardware (2.6 gate equivalents) and software. A 5-bit S-box (as used in Keccak’s S-box core) is used to enable a lightweight approach, and it has no known side-channel attacks. It can also achieve high throughputs, such as throughputs of between 4.9 and 7.3 Gbps. It stores its current state with 320 bits. Overall, ASCON won the NIST competition for a lightweight cryptography standard.
Now, ASCON has a chance to become a post-quantum cryptography standard for digital signatures with [here]:

Within the additional signatures looking to be standardized we see hash-based, lattice-based, code-based, multivariate polynomial-based, and isogeny-based methods. Within the previous standardization, two lattice methods (Dilitihum and FALCON) and a hash-based method (SPHINCS+) were selected for standardization. Now, ASCON-sign is being considered for standardization and is a hash-based method that uses the ASCON symmetric key encryption method. Overall, symmetric key encryption is seen to be quantum resistant.
Basically, ASCON-Sign is a variant of SPHINCS+, but uses ASCON as a foundation element. ASCON, itself, can implement both symmetric key encryption and hashing.
SPHINCS+
SPHINCS+ is a stateless hash-based signature scheme, which is quantum robust. It was proposed by Bernstein et al. in 2015 [paper][1] and updated in [2]. SPHINCS+ 256 128-bit has a public key size of 32 bytes, a private key size of 64 bytes, and a signature of 17kB. It has been shown to operate at speeds of hundreds of hashes per second on a 4-core 3.5GHz processor.
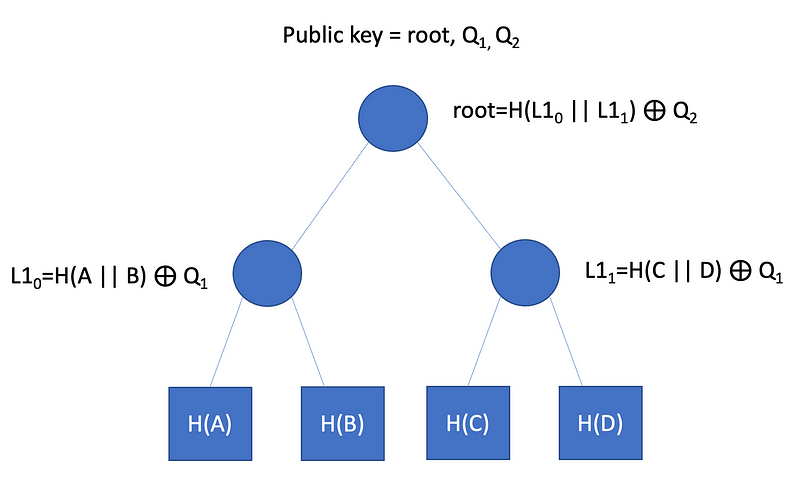
In this case, we will implement using SHA-256. SPHINCS+ uses many trees. In this case, the first tree is defined in a simpler way than a Merkle Tree, but we use a level mask. If we have four root nodes (A,B,C and D), and a first-level mask of Q1, we get two Level 1 nodes of:
L10=H((A||B)⊕Q1
and
L11=H((C||D)⊕Q1
We then create a root hash of Root=H((L10||L11)⊕Q2. The public key is defined with the root hash along and the bitmasks. Each of the leaves of the tree is then the public key for the WOTS+ L-trees using in SPHINCS+.
The following is an implementation of SPHINCS+:
import hashlib
import numpy as np
import binascii
def hashit(a,b,Q):
m = hashlib.sha256()
m.update(a+b)
m=m.digest()
c = bytes([aa ^ bb for aa, bb in zip(m,Q)])
return (c)
def printnodes(title,n):
print (title)
for i in n:
print (binascii.b2a_hex(i))
n_nodes=4
n_levels=2
node = [0]*n_nodes
Q = [0]*(n_levels)
level1 = [0]*(n_nodes//2)
for i in range (0,n_nodes):
node[i]=np.random.bytes(32)
for i in range (0,n_levels):
Q[i]=np.random.bytes(32)
i=0
for n in range(0,n_nodes,2):
level1[i]=hashit(node[n],node[n+1],Q[0])
i=i+1
pub = hashit(level1[0],level1[1],Q[1])
printnodes("Nodes:",node)
printnodes("\nLevel 1:",level1)
print("\nRoot: ",binascii.b2a_hex(pub))A sample run is:
Nodes:
b'b69c70c9d4e53008800fa00a5d3c7da7066ebadea7347eb1f94d0b52edd825a5'
b'cc12c073709d5be5095a0d4e81fae36b98a34e715cb747e990679c6ed8f7ae51'
b'8559e17789a1d4ddb2cc6d6515c1c0f3a594ad49570ddb39be6d920b799844dc'
b'bf5b092aab50616d290c43881715de5bd6aaa8b6adbf59554483769355dcdf9f'
Level 1:
b'a3e1c96fb6cbb684b8546b66791632c929f0d77e3bebde0339535488caf551c8'
b'782d270b840a84379ecbe871007855cf4d7114351b4962a2c0326fa8c58cff4c'
Root: b'e1e72492dd0adccb8c74a566261b013ebfbc1f079df35a50ad8e8bc35cf5a639'Overall, SPHINCS+ has a small key size, and where Level 1 (128-bit) security has a 32-byte public key (256 bits) and a 64-byte private key (512 bits). Unfortunately, the signature size is rather large at 17,088 bytes [here]:
Method Public key size Private key size Signature size Security level
------------------------------------------------------------------------------------------------------
SPHINCS+ SHA-256 128-bit 32 64 17,088 1 (128-bit)
SPHINCS+ SHA-256 192-bit 48 96 35,664 3 (192-bit)
SPHINCS+ SHA-256 256-bit 64 128 49,856 5 (256-bit)SPHINCS+ method
The method is:
- Initially we create 32 256-bit random numbers. These 32 values will be our private key.
- We then hash each of these values 256 times. These 32 values will be our public key.
- We now take the message and hash it using SHA-256. This produces 32 8-bit values (N1, N2 … N32).
- For the signature we take each 8-bit value in the hash of the message, and then hash 256-N times (where N is the value of the 8-bit value).
- To prove the signature, we take the message and hash it with SHA-256, and then take each 8-bit value. We then hash the 8-bit signature value by the number of times defined by the message hash value (N1, N2..). The result for each operation should equal the public key value.
This is illustrated below:

An outline here:
Conclusions
And, so, we have reached a point where we can use a symmetric key method with a hashed-based signature method. With this, symmetric key methods are seen a being safe against quantum computers, and so, since hash-based signatures are safe, we can have the performance enhancements of a symmetric key method with hash-based signatures (W-OTS). Of course, we are not really using symmetric key encryption — we are using the hashing function of ASCON, as this method gives us both hashing and symmetric key encryption with the same method.
References
[1] Bernstein, D. J., Hopwood, D., Hülsing, A., Lange, T., Niederhagen, R., Papachristodoulou, L., … & Wilcox-O’Hearn, Z. (2015, April). SPHINCS: practical stateless hash-based signatures. In Annual international conference on the theory and applications of cryptographic techniques (pp. 368–397). Springer, Berlin, Heidelberg [paper].
[2] Bernstein, D. J., Hülsing, A., Kölbl, S., Niederhagen, R., Rijneveld, J., & Schwabe, P. (2019, November). The SPHINCS+ signature framework. In Proceedings of the 2019 ACM SIGSAC conference on computer and communications security (pp. 2129–2146) [paper].