My Top 10 Most Interesting Things I Have Learned As An Academic

My Top 10 Most Interesting Things I Have Learned As An Academic
Well, an academic, of course, my advice for the New Year is to learn something new. And, not just learn it from a superficial point-of-view, go and dive into something and really learn it in depth. Why? Because it will make you feel better and (on average) will help you live a longer and more fulfilling life. It will change you and (hopefully) take away the stresses of modern life. In fact, the best way to avoid getting dementia is to continually learn and keep your mind active.
And I know I sound like a soap salesperson who is trying to sell you the benefits of bathing, but I passionately believe in the power of education. So, here are my Top 10 things I learnt about in my academic career. I have put them in order of how interesting and fulfilling they have been for my teaching and for me.
No 1: The Diffie-Hellman method
I have taught cryptography for over a decade, and it was the Diffie-Hellman method that hooked me. How could something that is so simple be so powerful? Once I saw its magic, I was completely switched on to the power of discrete logarithms and how they could protect our online world.

No 2: Transistors
Transistors were created within Bell Labs at the end of the 1950s, and have changed our world more than virtually any other invention While I studied electrical engineering in the 1970s, I was first exposed to the magic of the NPN and the PNP junction, and I still marvel at its operations. The transistor itself is made up of just three connections: Collector, Base and Emitter. The thing that you had to remember (for an NPN transistor) is that a small current from the Base to the Emitter caused a much larger current to flow from the Collector to the Emitter. This leads to a current gain, and where microamps can become milliamps. But, where they become most interesting is when they operated a switch, and where current flowed from the Collector to the Emitter or didn’t. The advent of CMOS methods then allowed us to control the switch with a voltage, and with virtually no current. We could then create a new perfect switch.
No 3: TCP, IP and ARP
When I understood how TCP, IP and ARP worked, I understood how the Internet worked.
The Internet changed the world of standardization, and where RFCs (Request For Comments) were used to draft proposals, and which were quickly adopted. Three of the greatest are TCP, IP and ARP. With ARP, we could resolve IP addresses to their physical address, and allow devices to connect to gateways and for gateways to find the destination host.
So while there is much debate around people like Tim Berners-Lee and Vint Cert, we should also include “The Editor of the Internet”: Jon Postel. Jon was born on 6 August 1943 and died in October 1998. Even up to his death, he was the editor of the Request for Comment (RFC) documents and administered the Internet Assigned Numbers Authority (IANA). He has since, in 2012, been inducted into the Internet Hall of Fame by the Internet Society, and the foundation he has left is as strong as any foundation ever created, in fact, it’s the foundation for our Cyber Age.
RFC (Request For Comment) documents are a way for standards such as for HTTP and email to become accepted quickly, and where organisations such as DARPA posting their thoughts for the standard, and quickly publish them based on the received comments. Developers could then go ahead and implement the system against the standards, without the massive overhead of taking them to international standards agencies like the ISO (International Standard Organisation) or the IEEE. With these agencies, a standard would take years to develop, and often involved the tinkering from countries, in order to protect their industries, and thus often stifled innovation.
While first published in 1969 (with RFC1), the classics first started to appear in 1981, and which now provide the core of the Internet:
- RFC 791 which defines the format of IP packets (IPv4)
- RFC 793 which defines TCP (Transport Control Protocol), and the foundation of virtually all of the traffic that exists on the Internet.
Many protocols, although now limited, became de-facto standards, and have moved on little since, including HTTP (HyperText Transmission Protocol) 1.1 which was initially created as RFC 1945.
So it was in September 1981 that the true foundation of the standardisation of the Internet communications was born:

Sandwiched in between the two classics, was another one, which did not have the same impact, but has helped to debug a billion systems: Internet Control Message Protocol (ICMP) — RFC 782. So RFC791, RFC792 and RFC793 has since changed the course of our societies.
The impact of the IP and TCP standards cannot be underestimated in terms of their impact on our society, and certainly rate alongside “The Wheel” and “The Transistor” as some of the most disruptive technologies ever created. Its standardization supported a whole range of activities, and basically allowed the Internet to boot up quickly. If nation-states had controlled the Internet, it would have ended up being licenced and locked down in its growth. Without the massive growth of the spread of the protocols, the Internet would have died as quickly as it had been created. With standards and government agencies controlling its every move.
If you are into networking, you’ll love subnetting and route aggregation:
No 4: Maxwell’s equations
I did my PhD around the computation of electromagnetic waves, and I was able to process Maxwell’s equation in the time domain (rather than in the frequency domain). For this, I had to code Maxwell’s equations and then step time in picoseconds. It was wonderful, and it opened my eyes to the beauty of these magical four equations.

No 5: Elliptic Curves
How can something so simple as an elliptic curve secure the Internet? Well, their use in ECC (Elliptic Curve Cryptography) was co-invented by Neal I. Koblitz and Victor Miller:

Both of them deserve the award as they discovered ECC independently of each other [1] here:

and [2] here:

Their idea came from preliminary work conducted by Lenstra on using elliptic curves to crack the RSA method:

Although they created ideas between 1985 and 1987, the main methods of ECC did not take off until 2005. The greatness of the method is the way we have scaled existing methods, such as the Diffie-Hellman method, to ECDH (Elliptic Curve Diffie Hellman), and is almost a drop-in replacement. For digital signatures, the ECDSA (Elliptic Curve Digital Signature Algorithm) method has now been adopted as a standard for many applications, including for Bitcoin transactions. Overall, poor implementation has led to problems, such as the discovery of the private key through side-channel analysis, but these have been overcome based on Peter Montgomery’s work at Microsoft on the multiplication process:
At the core of ECC is the simple equation of:
y² = x³ + ax + b (mod p)
and where p is a prime number. If you want to know more about these magical curves, try here:
And, here’s Neal:
No 6: Stick diagrams and Integrated Circuits
A while back, I taught integrated circuit design, and in those days we talked about transistors that were measured in microns. These days we now measure them in nanometers and can pack billions of transistors onto a silicon wafer that could fit on the end of your pinky. With a stick diagram, you could layout your transistors, just by crossing them between different layers:

What I loved about these stick diagrams was where two lines cross on different layers, leads to the creation of a transistor.
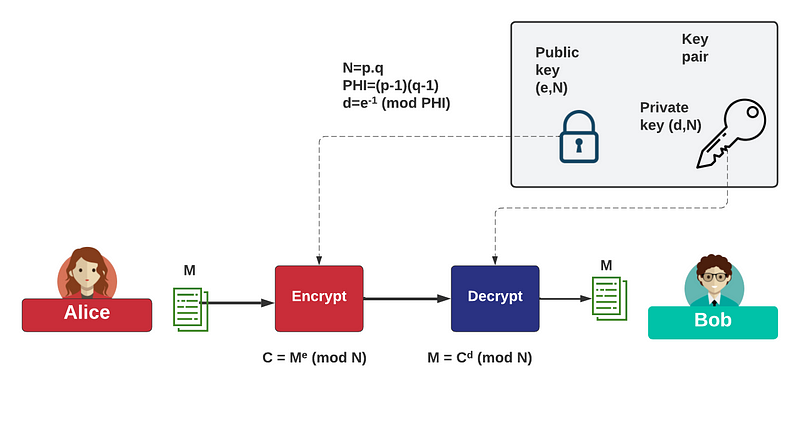
No 7: The RSA method
While the Diffie-Hellman method hooked me, it took a while for the RSA method to sink in, but once it did, it got me thinking more deeply about public key encryption (to encrypt with the public key and then decrypt with the private key) and digital signatures (to sign with the private key and verify with the public key). While created in the late 1970s, it is still one of the most widely used methods in public key encryption and in digital signatures. In fact, most of our online transactions use RSA to define the trustworthiness of a Web site. Together ECDH and RSA secure much of the Web.
No 8: Wireless Antennas
Radio waves have already intrigued me. Every time I click the remote for my car, I just imagine the propagation of the radio waves. And, with GPS, I still cannot quite understand how a tiny signal from three satellites can lead to location tracking with such accuracy. My PhD related to the design of patch antennas, and it was this work that allowed me to think deeply about how antennas were designed and operated. For this we have the mighty dipole antenna, where the antenna transmitted at a frequency which equalled half a wavelength. Thus for 2.4GHz, we have a wavelength of 8 cm. A dipole antenna is thus around 4cm in size for 2.4GHz:

Overall, wireless systems is a bit of a black art, and you can only guess how a system will actually work. And, then you have to understand things like dBms and mWatts, along with beam bandwidths and antenna patterns:

Find out more here: https://asecuritysite.com/wireless/wireless06
No 9: Routers
So it was 1981 when TCP and IP were created, and two major other things happened around the time that supported the growth of the Internet. The first was the release of the PC by IBM, and the other was when Leonard Bosack networked the Stanford University computer science department’s computers, along with Sandy Lerner. Their knowledge was then used to create the router, and the formation of Cisco in 1984. At its core was the implementation of the IP and TCP standards.
Often, it is love and war which advances innovation. And it is perhaps love that created one of the mightiest of technology companies: Cisco Systems. With that, it is alleged that Leonard Bosack and Sandy Lerner created routers as a way to send love letters to each other, as they didn’t have an electronic way to do so at the time.
Once Leonard and Sandy had created a prototype of a router, they went to their employer — Stanford University — and asked if the university wanted to commercialise their work. Overall, Stanford is one of the most innovative universities in the world and has created companies such as Google and Sun Microsystems. It is also one of the best places in the world to create a company which aims to disrupt our world. But the university spurned the chance — perhaps because Leonard and Sandy were not tenured academics and with a long track record of academic research.
In the 1980s, Leonard was a support engineer for Stanford’s mainframes and actually implemented the first campus-wide LAN at Stanford. This linked over 5,000 computers within a 16-square-mile campus, and which was a major challenge at the time due to compatibility issues. Sandy, too, worked for Standford as the director of computer facilities at the Graduate School of Business. And, after being rejected for their idea of creating the router, in December 1984, the couple registered “Cisco” — named after “San Francisco” and quit their jobs to focus on creating routers. The new home for their business was Menlo Park (and which would also become the home of Facebook at 1 Hacker Way, Menlo Park, CA 94025).
No 10: Finite/Galois Fields and Discrete Logs
I cannot begin to say what the magic of understanding finite fields did for my understanding of cryptography. Actually, it’s quite simple, and where we constrain our set of possible values within a finite field. This might be a finite field of {0,1,2,3,4,6} and where we limit our values to this set. Overall, in cryptography, we want to map from one set (A) to another (B), and then be able to map back from B to A with a reverse operation. This might be a multiplication operation from A to B, and then a divide from B to A. With this we often perform the (mod p) operation, and where p is a prime number. If we do this, we find out, that we can perform our normal maths operations, but constrain the results within a finite field. And so, these all work:
a.b (mod p) = a (mod p) . b (mod p) (mod p)
a + b (mod p) = a (mod p) + b (mod p) (mod p)
a * b (mod p) = a (mod p) * b (mod p) (mod p)
Find out more here: https://asecuritysite.com/gf/
It was John Napier who discovered logarithms, and where we have:
g^a . g^b = g^{a+b}
and:
(g^a)^b = g^{ab}
It is these basic operations — along with finite fields — that make much of cryptography work. Overall, we have operations such as:
g^a . g^b = g^{a+b} (mod p)
and where p is often a large prime number.
References
[1] https://labelslopez.weebly.com/blog/layouteditor-stick-diagram
[2] Koblitz, N. (1987). Elliptic curve cryptosystems. Mathematics of computation, 48(177), 203–209. Link.