The Five Eras of Cybersecurity

The Five Eras of Cybersecurity
I believe there are five eras of cybersecurity. In the first, we ciphered our messages using methods that were fairly robust against pen-and-paper attacks but struggled against the ever-rising power of computers, and in the most recent, we will break down most of the things that we have built over the past few decades — and thus build a more secure, resilient and privacy aware digital world.
Era 1: The Pen and Paper Era (aka The Stone Age of Cybersecurity)
And, so, where do we need to keep things secret? Well, basically, in times of love and war. For centuries, we have used ciphers to encode and scramble secret messages so that our adversaries cannot determine our motives or plans. Mary, Queen of Scots, for example, used her own cipher to send secret messages, and while her cipher looks a bit nieve these days, it was good enough for her at the time to evade prying eyes.
There were basically two types of this type of cipher. The first was simple, and just basically mapped our letters onto other letters or systems, and where only Bob and Alice knew the mapping. A more advanced method allows a secret key to be used by Bob and Alice and then generate the mapping based on this key.
But, computers came along, and they were fast at trying lots of different cipher permutations and different keys. And, so, once Eve had cracked the secret mapping, the cipher was cracked for good. This era of pen-and-paper ciphers ended in the 1970s, and was replaced by the encryption era.
If you want to try so of these ciphers, try here:
https://asecuritysite.com/encryption/ctf
Era 2: The Computing Era (aka The Industrialisation Era)
And, so, in the early 1970s, ciphers such as Playfair and scrambled alphabets, left the stage, and, through the work of Horst Feistel and others at IBM, the world finally found methods that properly protected messages. These contained ways of scrambling our plaintext through the usage of an encryption key and reversible rounds of computation — symmetric key encryption. In this way, Bob and Alice could share the same encryption key, and where the same key would encryption and also decrypt:

The world of proper cybersecurity was thus born, and it gave birth to the mighty DES. Before the time of the standardization of AES, we saw the birth of many ways of implementing symmetric key encryption, including TwoFish, Blowfish, 3DES and CAST. Each of these ciphers has its own features, such as having differing block sizes, and how they were constructed. With NIST standardizing AES, we finally had a single encryption method which allowed us to keep compatibility in our encryption process. But, there was a problem. How can Bob and Alice exchange their keys, without Eve listening to them? Well, the answer to this was solved in the public key era.
Some examples of this era are here: https://asecuritysite.com/symmetric/
Era 3: The Trust Era (aka The Human Era)
We entered into the Trust Eta in the late 1970s, and where Whitfield Diffie and Marty Hellman proposed a method of key exchange that allowed them to share public values — and then derive a secret. Eve could listen to these values being passed, but could not feasibly determine the shared secret:

This was one of the greatest breakthroughs in the history of computer science and named the Diffie-Hellman method. But, the method, too, pointed to the opportunity of having two encryption keys: a private key and a public key, where one key could encrypt and the other could then decrypt. And, so, it was Rivest, Shamir and Adleman (RSA) who then outlined the first practical public key encryption method:
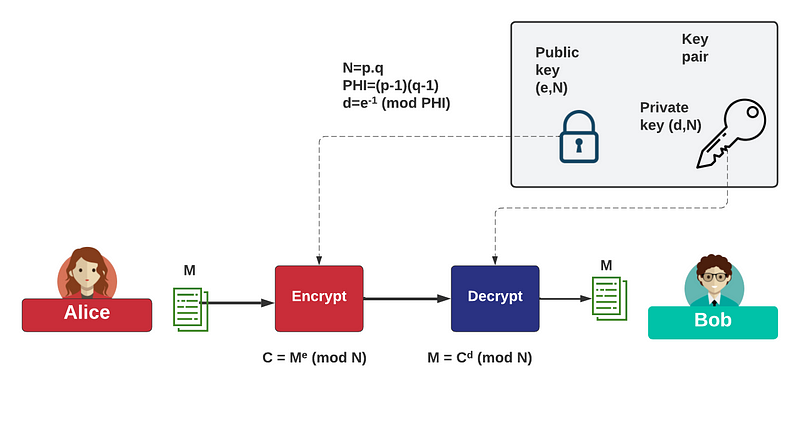
And, so, for the first time, we could actually expose our encryption key, and for there to be no information leaked. This public key encryption method thus opened the door to digital signing, and where Bob could sign a message with his private key, and then prove his identity with his public key.
Some examples of this era are here: https://asecuritysite.com/rsa/, https://asecuritysite.com/ecc/ and https://asecuritysite.com/dh/
Era 4: The privacy era (aka The Rise of The Crackers)
And, so, the end of the 1970s saw the rise of public key encryption. This provided a new toolbox of tricks for researchers, and the challenge was now how to use this toolbox to not only protect the secrecy of messages but also in the privacy of citizen data. Why should we log the IP address of a citizen? Why should a citizen reveal their password to someone that they don’t quite trust? The 1980s onwards, thus saw the rise of privacy methods, and in protecting sensitive information. Overall, the rise of the Internet accelerated the need for privacy, and companies harvested citizen data on production levels that had never been seen in the course of human history. It was George Orwell’s worst nightmare, and where no one could keep anything secret on the Internet.
And, it was Adi Shamir — fresh on developing the RSA method — who advanced cybersecurity with the additional of zero-knowledge proofs:

This gave rise to the Fiat-Shamir method, and where Peggy could get a secret, and prove that he knew the secret. The Pedersen commitment, too, allowed Bob to blind information, and not reveal it, but where it could still be used to process his information. And, where Claus Schnorr outlined a way of preserving privacy with digital signatures. All of these methods supported a non-interface element, and where Peggy could generate his own proofs, without being prompted with a challenge from Victor.
Some examples of the methods developed in this era are here: https://asecuritysite.com/zero/
It was the era of Peggy (the prover) and Victor (the verifier), and it is this era we are in now. But, this era will come crumbling down, and make way for the next era.
Era 5: Post Quantum Era (aka The Rebirth of Cybersecurity)
Like it or not, Peter Shorr showed that all the existing methods of the 3rd and 4th eras will crumble. This includes RSA, Elliptic Curve and Discrete Logs. And, Grover showed that the second era would also crumble unless we changed our approaches. The “attacker” is the humble quantum computer, and which can break all existing public key methods in production, and 128-bit symmetric key and hashing methods.
Some examples of this era are here: https://asecuritysite.com/pqc/
We are now at the dawn of this era. If you want to find out more, then come only to our session on 31 January at 6:30pm:
I am proud to be a Fellow of the BCS (FBCS) and honoured to be invited to give a talk hosted by the BCS Information…medium.com
It will be held on our Merchiston Campus (A17) at 6:30pm (UK time), and also hosted online.