Meet the King and the Queen of Cybercrime

Meet the King and the Queen of Cybercrime
I love radio and the spoken word, so podcasts are a dream to me. I love cycling on a cold and dank day and listening to them or putting them on in my car and just immersing myself in a beautifully told story. In fact, in my busy academic life, it’s possibly one of the few times I get a chance to really focus on something that isn’t academic or related to research. And, so, I’ve been listening to “The Crypto Queen” (Ruja Ignatova) on BBC Podcasts, and it’s one of the most intriguing podcasts I’ve ever listened to:
Dr Ruja Ignatova persuaded millions to join her financial revolution. Then she disappeared. Why? Jamie Bartlett…podcasts.apple.com

As a “crypto punk”, I believe in the power of public key encryption to change the world. But the history of our world shows that one of the things that humans love most is making money, and as much and as quickly as possible. And where there are opportunities to make money, there are many people who are ready to step forward.
The story of the Crypto Queen is that she created an elaborate fraud that has been valued at more than $15.8 billion, and then vanished from public view. In fact, she is the only female person on the FBI’s Ten Most Wanted Fugitives list:

While many building cryptocurrencies believed in the freedoms it gave to citizens from the profit-focused and greedy banks, there were some who were just in it to make as much money as they could. With the fraud, Ruja was the face of “OneCoin” and created a pyramid network of commissions in selling OneCoin. But this was not Bitcoin, and there is no cryptographic proof where a public ledger could verify the ownership of the coins. With OneCoin, there was no ledger, and the “coins” were just created and distributed. Basically, it was an SQL database, that could produce as many coins as needed.
And, so, the podcast of a queen brought back memories of Scotland’s most “successful” cipher criminal … a “King” named Glasgow-based Feezan Hameed [here]:

Meet King
It sounds like a script from a movie … a gang pays some money to someone working in a bank to give them the details of their customers (the target), and they then call them up and pretend to be their bank …
Hello. I am from your bank. It seems you have been hacked by a person named ‘King’ from Aberdeen. Everything is okay. Don’t worry. But please could you confirm your login and password, as we need to check it?
and the reply:
Oh dear. Thank you for that. My password is SalmondFish123.

Two days later, the target finds out they have no money in their account, and all their life savings have gone. At the same time, the fraudster is flying in a valet from Pakistan to polish their new Lamborghini.
This isn’t Hollywood … this is Glasgow!
While many people think that phishing emails are one of the greatest risks for fraud, it is vishing — the act of using the telephone to scam — that can have the greatest impact in terms of fraud. Many people still will give away the login details over the phone if they think they are talking to a trusted person.

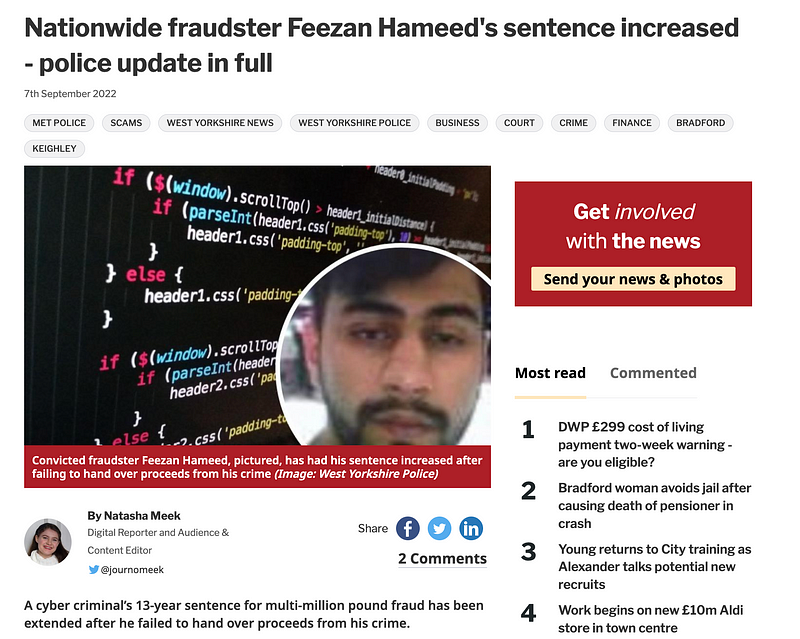
In the end, Feezan Hameed, also known as Feezan Choudhary, was jailed for 11 years. It is thought he made over £113m by scamming companies through a telephone scam. He then used the money to purchase supercars, mansions and expensive holidays. As a cover, Feezan, also known as ‘King’, pretended that he was a music producer, and owned a Bentley, Rolls-Royce, Lamborghini and his two Porsches.

His crime was that he defrauded over 750 UK firms, and he made around £3million every month. The crime involved cold-calling companies and telling them they had been hacked by someone called ‘King’ from Aberdeen, and then asking for the bank details (including their log-in name and password).

Within hours he managed to siphon off funds from their accounts, and also jammed the telephone network of the company with fake calls, in order that they did not get messages from their bank. So that the calls could not be traced, the gang used ‘burner’ mobile phones (which are often used by terrorists and criminals), which, once activated, were ditched after one day.
Insiders are the risk
He also paid insiders in the banks, such as Amy and Emma Daramola (see below), and who were Lloyds customer service assistants. Initially the asked for £50 for each record, but increased this to £250, in order to fund their desire to new clothes:

After receiving the details, Feezan would then contact the customers, and say he was from their bank. In one fraud, alone, he managed to steal £2.2million in minutes from a Gloucestershire-based solicitor’s firm. As solicitor firms often have a good amount of cash in accounts, they became a key target. Another solicitors’ firm in Liverpool lost £500,000 and one in Angelsey lost £670,000. Over £70million was syphoned from a bureaux de change in London and sent to Dubai and Pakistan.
His targets were from Lloyds, Santander, Barclays and RBS, and it is thought that the banks, in some cases, have been refusing to refund the customers, as it was their own fault in releasing the funds. Because of the speed of modern transactions, the funds were often laundered through Pakistan and then sent to money mules, which would convert the funds into cash.
In fact, in 2022, he had his sentence increased as he refused to pay back his gains: [here]
Conclusions
Please beware. Never give any details away on the phone. Unfortunately, people still fall for vishing scams, and businesses are often the target. Many of those involved in the fraud will not receive their money back, as it was their fault. For companies, the best course of action is to train staff to never give away bank details to those on the phone, or in email messages. The rise of AI will only make the risks worse.