ZKPs Made Easy: zkWeb and ZoKrates

ZKPs Made Easy: zkWeb and ZoKrates
This week saw the roll out of zkWeb, and which provides an easy way to produce Zero-Knowledge Proofs (ZKPs) [here]:

Basically, this infrastructure uses the zkokrates Javascript file ( zokrates.js) and which is an implementation of the ZoKrates toolbox for zkSNARKs on Ethereum. Basically a verifier submits key — such as a secret phase — zkWeb create a SHA-256 and converts this into a unique 14-digit hex string. This string is then passed to zokrates.js, and which uses some Solidity code to produce the ZKP.
NI-ZKP
We live in a digital world that gives too much away. Our systems are often set up to store sensitive information on us, and where we also pass this sensitive information through our applications. But, there is another way, and that’s the creation of Non-interactive Zero Knowledge Proofs (NI-ZKP). These magical little functions allow us to prove that we know something secret and give cryptographic proof for it.
So let’s take an example, and where Peggy has a secret value of x, and that Victor has stored a hash value such that:
y=H(x)
If Victor uses a 256-bit hash, there is virtually no chance that we will ever discover the value of x, with just the knowledge of y. x could thus be Peggy’s password, or my National Insurance number. It could even be the proof of a given 256-bit encryption key.
So let’s see if we can prove x with a knowledge of H(x), and run in a smart contract. As the smart contract can expose values, we need to keep the value of x secret. For this, we turn to Zokrates and Solidity.
Zokrates
ZKPs have been around since the mid-1980s, and have often been heavy in terms of their processing requirements. One new family has come along, though, and which provides fast and short proofs. This is zkSnark (zero-knowledge Succinct Non-interactive ARguments of Knowledge). Overall, zkSnarks have been used in applications of privacy-preserving cryptocurrency, but have applications within smart contracts, too. Normally we require a proof to be done using an off-chain method, but the zkSnarks now allows us to prove things on-chain — and in an efficient and low-cost way. As a result, we can create our off-chain applications, and then link them into the Ethereum blockchain for a proof.
One of the quickest ways to produce these proofs is to use Zokrates, and which can plug into Remix:

This code can then be compiled into Solidity code. The code to hash a value is given next:
import "hashes/sha256/512bitPacked" as sha256packeddef main(private field a, private field b, private field c, private field d, field h0, field h1):field[2] h = sha256packed([a, b, c, d])
assert(h[0] == h0)
assert(h[1] == h1)
return// Input: 'a' -> 0,0,0,97
// assert(h[0] == 45324487246557938747332883189457400843)
// assert(h[1] == 84478852209878349000735790184433475398)In Socrates we can only hold 128-bit values, and so our 256-bit hash is split into two parts. In this case h[0] for the lower 128 bits, and h[1] for the upper 128 bits. For the input data, we split into four 128-bit values, and which gives us a data input of up to 512 bits. The values of the input will be a, b, c and d, and where d is the end part of the data buffer. With many other cryptosystems, we use a big-endian format, and where the last byte as the first byte of the data. Thus for a data input of ‘a’, and for 16 bytes (128 bits), we end up with a hex value of:
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 61
and where ‘61’ is the hex value for an ‘a’. This is a value of 97 as an integer value.
With this, we have four private fields: a, b, c and d. These will be kept private to the smart contract, and will not be exposed, while h0 and h1 (the hash value) can be revealed:
def main(private field a, private field b, private field c, private field d, field h0, field h1):We will thus create a zero-knowledge proof for a, b, c and d and which relates to the hash values of h0 and h1. For the next part, we now need to compute a witness within the compiled program and which has the valid values computed. For this, we need to generate the values of h0 and h1 for the hash. So let’s take an into of ‘0x000….a’ and then compute the two input hash values (h0 and h1):
import hashlib
x = bytes.fromhex('00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 61')
hash = hashlib.sha256(x)
hx = hash.hexdigest()
print('hx: ', hx)
hh=bytearray(hash.digest())
i1=hh[:16]
i2=hh[16:]
val1=int.from_bytes(i1,'big')
val2=int.from_bytes(i2,'big')
print (val1)
print (val2)
print ()
print (hex(val1))
print (hex(val2))The run of this is:
hx: 22192dc09ba3afbc0d0c5b60675ab40b3f8e08fd3897de4e81a37a4752805f4645324487246557938747332883189457400843
844788522098783490007357901844334753980x22192dc09ba3afbc0d0c5b60675ab40b
0x3f8e08fd3897de4e81a37a4752805f46And so the two integer values we need for the witness are: h0=45324487246557938747332883189457400843, and h1=84478852209878349000735790184433475398. If we need to enter these values, we can generate the witness:

If we give it the wrong proof for the hash, we will generate an incorrect assertion:

Once computed, we can then generate a verification and a proving key. It can take over a minute, but is a once only compute. For this we get a file named verification_key.json:

The keys are then:
{
"alpha": [
"0x1f4acb288eb126d28ccf5216f575ce282f381e19b322c3a93be96394c3659d48",
"0x07a64b045e42a4e0ccd95edbbb072eada253fd76546b9e908ca5bb015458cacc"
],
"beta": [
[
"0x29896ca87ac917f4bbda0580d3cfad89b15a6c2b2f40eefd00332eb99183a186",
"0x2522995fa7f9a2e354021bcabdb601c32fa80ea869e91237ca8489a531e42eb7"
],
[
"0x2bb9455ee51a78e8a8ed2e2c393acdddddb78dded82618aab7be32e95dc01f82",
"0x037050b69e248d917620bc0ffa96f0ceab56356bbb00a4916ea189707b5fa87f"
]
],
"gamma": [
[
"0x1ae2285207b0875fd049c5f90e5bf38d3e0eec81615e355eb6ae86abc8e228fc",
"0x10ceff9a728f6a90db352e53670d2c8f0b8c967713f1fd4f78faab3aaa085e82"
],
[
"0x1ae77012927c158d58c0ad5885921f8c85a158d53fab02a47b55e6e34e67cee9",
"0x1e8b9e68d31f9179984583e89ecbb3b571cb2975b687e2f1983609d24aa42eef"
]
],
"delta": [
[
"0x3044d9d51ad9fc57aa18a5609c3504fb2d81af7c29b13d2a88efd5e39fa81378",
"0x19821f62e699a0a2d8b5e58cdb56bd5afed3921c2a1ae4141bf0c2fb6b89458b"
],
[
"0x0331f36c041bf4a3370906b3c509ab6f2360172c8166025fef8e85ba61d73435",
"0x2ccca119cbcfccc4d6de466dac8dbfeb8c53053f0b0629b73fc444036b531805"
]
],
"gamma_abc": [
[
"0x1fb042cd7e2f84f28a68723e5539525f9059c334ae477617548723d8acba6cdd",
"0x1809fa116526d57230bd58d42333992f139969b720f3241464cd184110a8248f"
],
[
"0x05a2b587d4d1c11c7fe81e9483eaa3c3c3fb7a2d7d9e1c123fa261d1b9dc1f1b",
"0x22b9ba436a4db558617989b064a0f8d89420fb5f121b48df7cc8591e11c1ef53"
],
[
"0x119a8bb852c8c5cfdb4e125660bcb22b172050148b6f9e9e3ca9280926b1cb03",
"0x1fe6063a3a48b833156592adc8b0dde752631db2f3ab9ee5c3819c354831d583"
]
]
}With the verifier and proof keys, and the witness, we can now generate our proof:

We now have a verifier proof (proof.js):
[["0x0a3bb1b06802e0bddf2f719a2adadfbda2bf628bcc469f97849f3a2009266ee1","0x1f0e7ef4eafe8acfb8e6f1d608699dc4db47d7553c4a9e6a1630ffe8236be4ee"],
[["0x2114b641d3de45ac6f59377e5f79ea4e9535276485a0814015c4993cfa367530","0x04bfaabe99401fe960026098f2c994428758132737059ce222b4bf59347e8680"],
["0x12af358a294385f705eccef47e01cf89a681b0de94387a35000ff85b8c99b79b","0x032ee889089f107a4214218d08736f31b523799021f700a1c80aab0e9609ed4c"]],
["0x293557474f9044afdd3d825609ff22b2659c773cfca55ae9fe51c8b555218a0b","0x19e45a09b7548dac68bebca92325e3e1415b34320e715e7b844fb4417b1110fd"]],
["0x0000000000000000000000000000000022192dc09ba3afbc0d0c5b60675ab40b","0x000000000000000000000000000000003f8e08fd3897de4e81a37a4752805f46"]The first part of this file gives us the proof and the second part gives the inputs. We will need these two parts for testing. The first four lines is the triplet will use for the proof and the rest is the input of the hash:
[["0x0a3bb1b06802e0bddf2f719a2adadfbda2bf628bcc469f97849f3a2009266ee1","0x1f0e7ef4eafe8acfb8e6f1d608699dc4db47d7553c4a9e6a1630ffe8236be4ee"],
[["0x2114b641d3de45ac6f59377e5f79ea4e9535276485a0814015c4993cfa367530","0x04bfaabe99401fe960026098f2c994428758132737059ce222b4bf59347e8680"],
["0x12af358a294385f705eccef47e01cf89a681b0de94387a35000ff85b8c99b79b","0x032ee889089f107a4214218d08736f31b523799021f700a1c80aab0e9609ed4c"]],
["0x293557474f9044afdd3d825609ff22b2659c773cfca55ae9fe51c8b555218a0b","0x19e45a09b7548dac68bebca92325e3e1415b34320e715e7b844fb4417b1110fd"]]
["0x0000000000000000000000000000000022192dc09ba3afbc0d0c5b60675ab40b","0x000000000000000000000000000000003f8e08fd3897de4e81a37a4752805f46"]Finally, we will create our Solidity smart contract with an export:

The code is then:
// This file is MIT Licensed.
//
// Copyright 2017 Christian Reitwiessner
// Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions:
// The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software.
// THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
pragma solidity ^0.8.0;
library Pairing {
struct G1Point {
uint X;
uint Y;
}
// Encoding of field elements is: X[0] * z + X[1]
struct G2Point {
uint[2] X;
uint[2] Y;
}
/// @return the generator of G1
function P1() pure internal returns (G1Point memory) {
return G1Point(1, 2);
}
/// @return the generator of G2
function P2() pure internal returns (G2Point memory) {
return G2Point(
[10857046999023057135944570762232829481370756359578518086990519993285655852781,
11559732032986387107991004021392285783925812861821192530917403151452391805634],
[8495653923123431417604973247489272438418190587263600148770280649306958101930,
4082367875863433681332203403145435568316851327593401208105741076214120093531]
);
}
/// @return the negation of p, i.e. p.addition(p.negate()) should be zero.
function negate(G1Point memory p) pure internal returns (G1Point memory) {
// The prime q in the base field F_q for G1
uint q = 21888242871839275222246405745257275088696311157297823662689037894645226208583;
if (p.X == 0 && p.Y == 0)
return G1Point(0, 0);
return G1Point(p.X, q - (p.Y % q));
}
/// @return r the sum of two points of G1
function addition(G1Point memory p1, G1Point memory p2) internal view returns (G1Point memory r) {
uint[4] memory input;
input[0] = p1.X;
input[1] = p1.Y;
input[2] = p2.X;
input[3] = p2.Y;
bool success;
assembly {
success := staticcall(sub(gas(), 2000), 6, input, 0xc0, r, 0x60)
// Use "invalid" to make gas estimation work
switch success case 0 { invalid() }
}
require(success);
}
/// @return r the product of a point on G1 and a scalar, i.e.
/// p == p.scalar_mul(1) and p.addition(p) == p.scalar_mul(2) for all points p.
function scalar_mul(G1Point memory p, uint s) internal view returns (G1Point memory r) {
uint[3] memory input;
input[0] = p.X;
input[1] = p.Y;
input[2] = s;
bool success;
assembly {
success := staticcall(sub(gas(), 2000), 7, input, 0x80, r, 0x60)
// Use "invalid" to make gas estimation work
switch success case 0 { invalid() }
}
require (success);
}
/// @return the result of computing the pairing check
/// e(p1[0], p2[0]) * .... * e(p1[n], p2[n]) == 1
/// For example pairing([P1(), P1().negate()], [P2(), P2()]) should
/// return true.
function pairing(G1Point[] memory p1, G2Point[] memory p2) internal view returns (bool) {
require(p1.length == p2.length);
uint elements = p1.length;
uint inputSize = elements * 6;
uint[] memory input = new uint[](inputSize);
for (uint i = 0; i < elements; i++)
{
input[i * 6 + 0] = p1[i].X;
input[i * 6 + 1] = p1[i].Y;
input[i * 6 + 2] = p2[i].X[1];
input[i * 6 + 3] = p2[i].X[0];
input[i * 6 + 4] = p2[i].Y[1];
input[i * 6 + 5] = p2[i].Y[0];
}
uint[1] memory out;
bool success;
assembly {
success := staticcall(sub(gas(), 2000), 8, add(input, 0x20), mul(inputSize, 0x20), out, 0x20)
// Use "invalid" to make gas estimation work
switch success case 0 { invalid() }
}
require(success);
return out[0] != 0;
}
/// Convenience method for a pairing check for two pairs.
function pairingProd2(G1Point memory a1, G2Point memory a2, G1Point memory b1, G2Point memory b2) internal view returns (bool) {
G1Point[] memory p1 = new G1Point[](2);
G2Point[] memory p2 = new G2Point[](2);
p1[0] = a1;
p1[1] = b1;
p2[0] = a2;
p2[1] = b2;
return pairing(p1, p2);
}
/// Convenience method for a pairing check for three pairs.
function pairingProd3(
G1Point memory a1, G2Point memory a2,
G1Point memory b1, G2Point memory b2,
G1Point memory c1, G2Point memory c2
) internal view returns (bool) {
G1Point[] memory p1 = new G1Point[](3);
G2Point[] memory p2 = new G2Point[](3);
p1[0] = a1;
p1[1] = b1;
p1[2] = c1;
p2[0] = a2;
p2[1] = b2;
p2[2] = c2;
return pairing(p1, p2);
}
/// Convenience method for a pairing check for four pairs.
function pairingProd4(
G1Point memory a1, G2Point memory a2,
G1Point memory b1, G2Point memory b2,
G1Point memory c1, G2Point memory c2,
G1Point memory d1, G2Point memory d2
) internal view returns (bool) {
G1Point[] memory p1 = new G1Point[](4);
G2Point[] memory p2 = new G2Point[](4);
p1[0] = a1;
p1[1] = b1;
p1[2] = c1;
p1[3] = d1;
p2[0] = a2;
p2[1] = b2;
p2[2] = c2;
p2[3] = d2;
return pairing(p1, p2);
}
}
contract Verifier {
using Pairing for *;
struct VerifyingKey {
Pairing.G1Point alpha;
Pairing.G2Point beta;
Pairing.G2Point gamma;
Pairing.G2Point delta;
Pairing.G1Point[] gamma_abc;
}
struct Proof {
Pairing.G1Point a;
Pairing.G2Point b;
Pairing.G1Point c;
}
function verifyingKey() pure internal returns (VerifyingKey memory vk) {
vk.alpha = Pairing.G1Point(uint256(0x1f4acb288eb126d28ccf5216f575ce282f381e19b322c3a93be96394c3659d48), uint256(0x07a64b045e42a4e0ccd95edbbb072eada253fd76546b9e908ca5bb015458cacc));
vk.beta = Pairing.G2Point([uint256(0x29896ca87ac917f4bbda0580d3cfad89b15a6c2b2f40eefd00332eb99183a186), uint256(0x2522995fa7f9a2e354021bcabdb601c32fa80ea869e91237ca8489a531e42eb7)], [uint256(0x2bb9455ee51a78e8a8ed2e2c393acdddddb78dded82618aab7be32e95dc01f82), uint256(0x037050b69e248d917620bc0ffa96f0ceab56356bbb00a4916ea189707b5fa87f)]);
vk.gamma = Pairing.G2Point([uint256(0x1ae2285207b0875fd049c5f90e5bf38d3e0eec81615e355eb6ae86abc8e228fc), uint256(0x10ceff9a728f6a90db352e53670d2c8f0b8c967713f1fd4f78faab3aaa085e82)], [uint256(0x1ae77012927c158d58c0ad5885921f8c85a158d53fab02a47b55e6e34e67cee9), uint256(0x1e8b9e68d31f9179984583e89ecbb3b571cb2975b687e2f1983609d24aa42eef)]);
vk.delta = Pairing.G2Point([uint256(0x3044d9d51ad9fc57aa18a5609c3504fb2d81af7c29b13d2a88efd5e39fa81378), uint256(0x19821f62e699a0a2d8b5e58cdb56bd5afed3921c2a1ae4141bf0c2fb6b89458b)], [uint256(0x0331f36c041bf4a3370906b3c509ab6f2360172c8166025fef8e85ba61d73435), uint256(0x2ccca119cbcfccc4d6de466dac8dbfeb8c53053f0b0629b73fc444036b531805)]);
vk.gamma_abc = new Pairing.G1Point[](3);
vk.gamma_abc[0] = Pairing.G1Point(uint256(0x1fb042cd7e2f84f28a68723e5539525f9059c334ae477617548723d8acba6cdd), uint256(0x1809fa116526d57230bd58d42333992f139969b720f3241464cd184110a8248f));
vk.gamma_abc[1] = Pairing.G1Point(uint256(0x05a2b587d4d1c11c7fe81e9483eaa3c3c3fb7a2d7d9e1c123fa261d1b9dc1f1b), uint256(0x22b9ba436a4db558617989b064a0f8d89420fb5f121b48df7cc8591e11c1ef53));
vk.gamma_abc[2] = Pairing.G1Point(uint256(0x119a8bb852c8c5cfdb4e125660bcb22b172050148b6f9e9e3ca9280926b1cb03), uint256(0x1fe6063a3a48b833156592adc8b0dde752631db2f3ab9ee5c3819c354831d583));
}
function verify(uint[] memory input, Proof memory proof) internal view returns (uint) {
uint256 snark_scalar_field = 21888242871839275222246405745257275088548364400416034343698204186575808495617;
VerifyingKey memory vk = verifyingKey();
require(input.length + 1 == vk.gamma_abc.length);
// Compute the linear combination vk_x
Pairing.G1Point memory vk_x = Pairing.G1Point(0, 0);
for (uint i = 0; i < input.length; i++) {
require(input[i] < snark_scalar_field);
vk_x = Pairing.addition(vk_x, Pairing.scalar_mul(vk.gamma_abc[i + 1], input[i]));
}
vk_x = Pairing.addition(vk_x, vk.gamma_abc[0]);
if(!Pairing.pairingProd4(
proof.a, proof.b,
Pairing.negate(vk_x), vk.gamma,
Pairing.negate(proof.c), vk.delta,
Pairing.negate(vk.alpha), vk.beta)) return 1;
return 0;
}
function verifyTx(
Proof memory proof, uint[2] memory input
) public view returns (bool r) {
uint[] memory inputValues = new uint[](2);
for(uint i = 0; i < input.length; i++){
inputValues[i] = input[i];
}
if (verify(inputValues, proof) == 0) {
return true;
} else {
return false;
}
}
}Now let’s test it by using the ganche blockchain:

We then use the Solidity code we generated before, and compile it:

Next we can deploy to our local blockchain:

And the test:
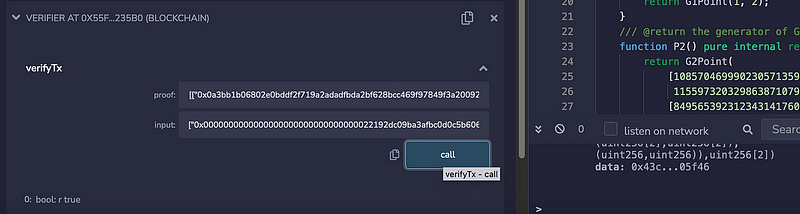
We can see we get a true return. But if we use an incorrect proof, we get a false return:

And so we have proven, that we know x for H(x). We can now deploy our smart contract to the Ethereum test network:

This will then create a new smart contact:

And where we must verify the code:

with:

And where we paste our code:

and then get a successful creation:

We can then test it on the test network [here]:

And testing:

The contract is here:
https://ropsten.etherscan.io/address/0xb3a18b87eabf5abe13cd9dcd9ee7484df2ccaffc
and with the proof of (for 0,0,0,97):
[["0x1538d0c6469863c256046d405e63952ee0d89b273ac3f9602b3581b9523470c8","0x22134f7e8bfbedba329b37b85cbf80435f266b4743ebbaa6dff577b31f99988f"],[["0x0a85811072aa12eae07d1b783717bdf5a02dadc967ad74b341acd446ba458d9f","0x2c7805c9d1ff6db5f42acb31fa88f67a07327a9a5bb2064df06fde63d109310c"],["0x27f25ac8fd5e204b53fd887667ebf3fb77165bedec4ca845bf220e1926f9dcec","0x0c9061c11b315a9d31a6a22135a5a2cbd95a08e3dac0a276809134926b8596dd"]],["0x1f0f16fb33b5627c0fc309e4387ca4982a28bbdb3a6bef57a4a23d406d9921a8","0x072b8f9dc482c7c9a5512382aa8924f18e263789686dd278b90354963ceba89c"]]And input hash value:
["0x0000000000000000000000000000000022192dc09ba3afbc0d0c5b60675ab40b","0x000000000000000000000000000000003f8e08fd3897de4e81a37a4752805f46"]Here is a demo: