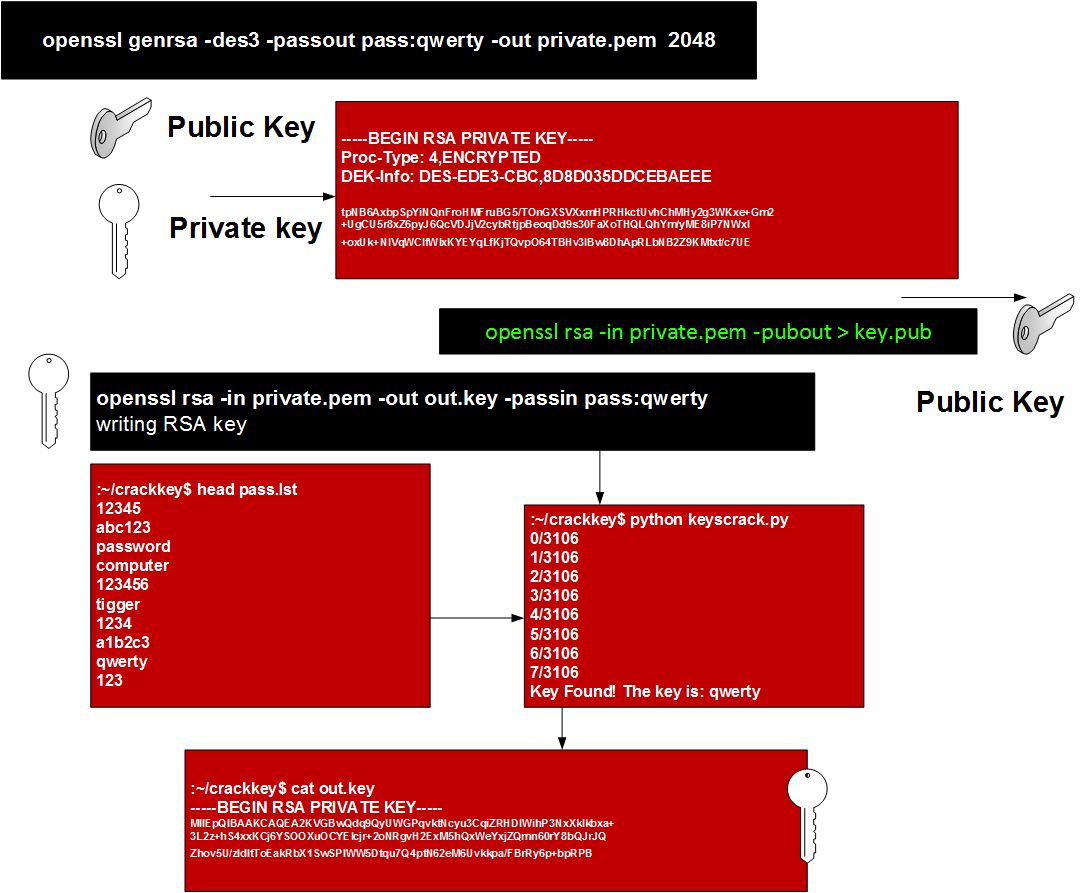
Cracking the Private RSA Key[Back] One of the weakest things about cryptography is that you might have a strong encryption key (such as a 128-bit or 256 bit key), but you create it from a pass phrase, or where you protect it with a password. This considerable reduces the strength of the key. For example, if our password is generated from a list of 1,024 words, we only have an equivalent key size of 10 bits. For one million passwords, it rises to 20 bits, which is considerably shorter than a 128-bit key. The overhead is the time taken to try the key. So let's look at cracking the private key. The RSA private key can be stored in a PEM file format. This applies a passwords onto the private. Unfortunately this can often be cracked with a brute force or dictionary attack.The method we can use is illustrated below:
First we generate a private key and setup a password of "qwerty": :~/crackkey$ openssl genrsa -des3 -out private.pem 2048 Generating RSA private key, 2048 bit long modulus ....................+++ ...+++ e is 65537 (0x10001) Enter pass phrase for private.pem: qwerty Verifying - Enter pass phrase for private.pem:qwerty Note that we can also use the "-passout" optionn to automate the password:
openssl genrsa -aes128 -passout pass:qwerty -out private.pem 2048
Next we will list the key:
:~/crackkey$ cat private.pem
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: DES-EDE3-CBC,8D8D035DDCEBAEEE
tpNB6AxbpSpYiNQnFroHMFruBG5/TOnGXSVXxmHPRHkctUvhChMHy2g3WKxe+Gm2
+UgCU5r8xZ6pyJ6QcVDJjV2cybRtjpBeoqDd9s30FaXoTHQLQhYm/yME8iP7NWxl
+oxUk+NlVqWClfWlxKYEYqLfKjTQvpO64TBHv3lBw8DhApRLbNB2Z9KMtxt/c7UE
ULzJDYCxQWpYmhP2YcDUp/juOCjxoRAicVDiW2F6MbfXiy3urlMV81frHpcjkwPW
FcetsPr5pBhypdY9nf3zQYQsXyw1X/OlcINPZsTJpIyyd1JYEfWQ0Wyye7Y0Oy45
0jlxKMRrfCeWgo3RhuYGDuRqpJdB++3t1WWY/A1ml6VqX77ZX00lNRDpESnw5lYd
R1pVO9lvsVXExrP/CoUpn3IjGc+hEKyMZzXXnpMpCjg1K5SppJT018n9Yqwa0kVw
FFxKPqoPo4M7o4KuAgYzrE8ntenIm0H9F9UDBWenbGVSOmzlAt+ONmpwQwNd54E7
vSc47m6AON7cHK9d3AzkSwZD19WofQYSEupaa2InCu1FTrca9HB7aKSK94+3Tq97
aWzajJk2eMWUcyEWzO5sR5jmJMthPBQYHio3z02aLhRoUBrA2iMUAY2wKniUnk1b
v3U8P1GRE9VIscchbyQvbQh4SlLUGlg7t5oixBwUYZgG7zdWmHmsiDtCWlpqhsCR
2Gx5suA/luRJG6OG2AZjkW5YKgkjAjQlqS+WduB/cWHHBBKlRwc/vXzt8tEUs+5q
bT3jgPUIh4swWtK7o76XibSMq1FWCMOFSGXMKG2x4fjjLmXRQpzwfgPLxSnPdfi0
XjuVEcRyAgJDpNzCpile33VYT9iWGQl2WHGQ7OjYTeGejER5AKalHLYR1weUC5rV
yRTdCdwAf2QfagSu8iB+PhIWi6sVemTD95pmgX/FT5sry/8kIGM9ofmGuBz2OtFa
hRi2xcHtmiCajwwXY6chLYH0D9AcHNZVPyQ1g620e2OhLuLyCLYZ29mpplIsTLT+
IY2FVRbp4hwnuJFWUGKfEHwJSi6pM21/yzvG80E5Zarnroza8iFcFE31G9Hzsy6Q
jAf0niY8xG9LrXQwPLgvSTkAsgprMYOvNoDPyYISqxnAN8hyWzg2SwcSBYTt+gsu
U2uU4PZyQZcZMAx/ipxPqznVjJERPNswMdrulXjHi/ogRotItmnGqjRl6UY3IS70
uKhdk0vpmRGcsMGa7DjqGRcCPptnFn6A8ASJeuP1qga4WCFOTJeBs8kGP9HiTy/N
DlnxhlQHDWNdLlUwKmOW5pqgrM12hLVf4TVTR7wjUuC7wzBp/1bhaiUifr8p8Ie0
mvC9Pz79TWg7oKCZCkdOv6valYqtwFXN7mu/a/neHOFh7Tqao9q5+iK1zdpwX1jv
ESn/O/zOFCFcK1Q2M66P9rvGqv73U2zyO22219LpbEqWh0IHARmikaZgS6XLHGVZ
mNQyjfDsO55zJHVOVA6+pw2W09fZVBS1xgV4hK3q3Egx2KytLzVtcOeTK+2MZTwb
aMBMYui04Dc4PklgwUO7cSpMG9GhBn3W0cNx8ppBXwCDFnGyaA5kfG3HjaFcseDn
-----END RSA PRIVATE KEY-----
In this case we have encrypted the key with DES-EDE3-CBC (3-DES) and with a salt of "8D8D035DDCEBAEEE" (as we used the -des3 option, and where other options include -aes128, -aes192, -aes256, -des, and -idea). Normally we would export the public key with: :~/crackkey$ openssl rsa -in private.pem -pubout > key.pub Enter pass phrase for private.pem: qwerty writing RSA key :~/crackkey$ cat key.pub -----BEGIN PUBLIC KEY----- MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAsp0LoOvjc5eyjcFD6wJy SvQRBf6E++VbXCKWhB2X387j6vwjP0wKxw5BVrvFf/YfLBZnN30a598vr3exhxii A6r8pMl4mxkuNSn0EfPHHWACdmdBCBMhOqvnjivaAXoy9P857EY1jRJGmP+04Wcd Pi74dVNfMlJ6h37+iQl2k5c94+A3AtDw2+lNDZx621zOUa3fUjH1ECk6eBBMITt6 C18CxzigoKGau+bXxusWtbY6illKNOFskQNrED9F2qZdt6882bzc/wXVyELBVHqk MgbjNTGW+bH9CpIsnuTdL/TCg0Ade6KUaBqOww42CJt0nmPD0ubs82Pyd/2b6krc VQIDAQAB -----END PUBLIC KEY----- If we try the wrong password on the private key file we get an exception:
:~/crackkey$ openssl rsa -in private.pem -out out.key -passin pass:password123
unable to load Private Key
140735838671752:error:06065064:digital envelope routines:EVP_DecryptFinal_ex:bad decrypt:/BuildRoot/Library/Caches/com.apple.xbs/Sources/libressl/libressl-22/libressl/crypto/evp/evp_enc.c:529:
140735838671752:error:0906A065:PEM routines:PEM_do_header:bad decrypt:/BuildRoot/Library/Caches/com.apple.xbs/Sources/libressl/libressl-22/libressl/crypto/pem/pem_lib.c:486:
Next we will try the correct password:
:~/crackkey$ openssl rsa -in private.pem -out out.key -passin pass:qwerty
writing RSA key
and the message we receive is "writing RSA key". We thus just need to write a Python program which reads-in a dictionary file, and then detects the "writing RSA key" message. We now use a dictionary file (pass.lst [link]):
:~/crackkey$ head pass.lst
12345
abc123
password
computer
123456
tigger
1234
a1b2c3
qwerty
123
And then run some Python code:
:~/crackkey$ python keyscrack.py
0/3106
1/3106
2/3106
3/3106
4/3106
5/3106
6/3106
7/3106
The key is: qwerty
And we have cracked the key. If we view the key, we get (out.key):
:~/crackkey$ cat out.key
-----BEGIN RSA PRIVATE KEY-----
MIIEpQIBAAKCAQEA2KVGBwQdq9QyUWGPqvktNcyu3CqiZRHDlWihP3NxXklkbxa+
3L2z+hS4xxKCj6YSOOXuOCYElcjr+2oNRgvH2ExM5hQxWeYxjZQmn60rY8bQJrJQ
Zhov5U/zIdItToEakRbX1SwSPIWW5Dtqu7Q4ptN62eM6Uvkkpa/FBrRy6p+bpRPB
Z/28VAcMUVyRAUIYV8yFRY+gP3i3T1rnhEeax4omNrXN7bcw/znRxdTl2wplliMw
sJ9EXKucz4+d9xSjFK9qvsinU2xk4/5q2Sh+2TTqpvT8dYQZQl/SPBAolyT2wo+w
IQoHjvOq/L3buGubHNpfzl2hOrfWHnCCMGUvmwIDAQABAoIBAQC9UUAupWQgYeBO
yYi4ieL+Ho23i/I5jBp0F+jA/+rT0CLaCPBlCcmbAjyuifhZ+2/1FMjlfCOJmPjO
zVAoI+dRluukK4Us4EHxTMOrybIfEP+YsT4c20l7hDAdIAPDlIJYw7N8b3TIOp0v
eNS+jrDq5+d1PGIdW+awezcbstixOYkGi+MMGjPn0sHxr0G11B6GEzXy4JbQTatF
QD9Q6o8oO1p+0NS0WBaMnDdHQ9bmpVYA4LJHP+wIePZKJgNPpjaXOvNtD/4HRUwW
W/zuMEUs6D35k8VwhPfe5yo6ixGO7lZaen1cpXy/JjAELC434N2LpWeeZW6sIjtp
q03dmLMRAoGBAPMO15gvkNFQ5fYA4q/SQINX5QUSPy0xLp58uxCp/nMopB1Adroy
qXu/rvySmnizNHSOCYUwMOJg5VibpiezdzzNVPgYI3egrL7RnIUQ7fP2bu9McnSl
KI2i8GYXwWatxBnoIaZjRDUQsxDjnV3GNoHK0qT5PDQb1paGoCh1HNwvAoGBAOQu
ZoeugDXytlWZcuZtNlO8aF0HmD+zKSeR35IdrUZTkSLw681XBy/JgvdMzQaJ88xw
VrwRZOaHHE13/VIDdCz1DX9WP9z6jLX6ULfGiuYouS9CuK0cWMEcrnjR+O6V2fWt
IGTYSQn2tQqpVHoaA0vP1xAqsQ/sA/uWCBXRiCxVAoGBAJ/GbPDsq6z9Gf3pvRpJ
AwGUIMeBpCgIAZZLdgjRRqPa3m8gNivWK9VePyBnGsYnP18zE40LDcdyXLEvuDy2
27YLYESqUX5ND+FsFxDd/R33LBuATGjjPNJGfvMNwKPHrHY/QweGj4q2jI+YoJTJ
PIF7m5a5A9tZRWmz28pcmfkfAoGANmmKMZi/Ih46tLbe22v3pIgtKuIAwE/s5G64
rZM+GqMa3QYudMzn/dFD1c0OpxyGcp3nUPmk4gQeD6spUUFZls7o5RCgMgXdQBfs
36YMwU28uzRh7YXw9DvurwkDH4HEc/1Q2DtrT2DxUxWF+4fweUeatVQ43N8fJANm
8i0BF/ECgYEA7EMU9jdNgb0aBZLqrRZpBWa2WFreUsA9aLc8oeM6XxdOPi7DDW5S
merJ7GhaucXP+eafnG5iB5xb/CpJWI4RwalknhaTmEpLO+vwFeSv8fuTRhq4ySO+
woSIOMMkyvF5HVy0Osxy203tTtj2/Y+0anJd79ZmdRqgVT5doF4jLM0=
-----END RSA PRIVATE KEY-----
Python codeThe Python code used is:
from subprocess import PIPE, Popen
import subprocess
import sys
def cmdline(command):
proc = subprocess.Popen(str(command), stdout=subprocess.PIPE, stderr=subprocess.PIPE, shell=T$
(out, err) = proc.communicate()
return err
def main():
words = [line.strip() for line in open('pass.lst')]
print("\n")
count=0
for w in words:
strcmd = "openssl rsa -in private.pem -out out.key -passin pass:"+w
res=cmdline(strcmd)
if res.startswith("writing"):
print("\nThe key is: "+w)
sys.exit()
print(str(count)+"/"+str(w))
count=count+1
print("\n")
if __name__ == '__main__':
main()
PresentationPuzzleCan you solve the password on the following [file]: -----BEGIN RSA PRIVATE KEY----- Proc-Type: 4,ENCRYPTED DEK-Info: AES-128-CBC,15D541B6D82BC43C51240532FBCFD84F TJFHpBez3sMkQIiA7JOw+7sjnr87Vpq98eRqWtOgSGjXWQ6f0fjx+PZ6DoBaI2pE JcMbINBvGlOyk66/GGWrowgJnipzj4UTOtWRp7k38PETBwNt+1o2cZ8nB8emyjVz 0JnZ3Skf1NZnf4SOVvwYhOwGRPS89bbRFUN/HPg/46Km+GEJjmzipRKoyZZpPNdu I/0pCdyTZypuciF8IzKMnrQA0k2llEG4no5/pGYz+SJ/Y+32Tdl1cpoCeND03NYL bjye2EL1wC+ecXAFWlAKrze/Xk2Ed18sigBSRjgBLWPh9kcWTXDnvELriIotlHa5 qAGbxShHTI4Xeci7VepUW+WdNGuDtBgUbCn47tKZrA0aXp71re8AQOLO6pKlSL3r bsl3ps7pk/q9CF9fdyhcHygCddhPi96qhhaV5hqI1tM4XW+BC0yLAkzMIRHfgaBy kEwr2v6fC6IT4lEAlpl9ebbXlLUXLkex8+pnpa+BsLHbqxKXn6evl7stO3RjrXNk DbGptzj5rKOONu12KxYk5v3B0IjB7plFY/8c1yVELwuLHv2nFSClewOUS6WW9GI7 yqdC/2HQ0bGOga9IOC9KISnwIaTADJfi3UO1J+WJnPBte508a7BHNxKG80QZuggT OmVzebiOn0aIAs5WlpLPcYbcsPCDAucNk0fKMynu5uHhAnpxQntGf1MzfoZs+aZD 0LpwztfNPw66dWF6LrU0bn59B3X764XfmgSi3mx9AGz4DEP51pWe8fUmLztcWnze dvXtmb2Qu21BgCl79wwsTMXs1kDYeUqNk6r1B6S9u5LT0v1lfcfcDx+0YKWCs0hN g94MrnpV/EnIwdCHs4u5FeZEAveinHFNqAqJerdq9uJBBCShJi3QXp1y4Z/Z2GL3 /N47hNDDZ3o8IoRZiKRVi4UgH8Niavfjbk+AJ5710AudzzgYyePo906WMOVVCvaL nzmhdV+phXfA6Scb8wStoZtimrNnJWZoByLwJUdWHcqa735uewUfUnHcVp3StCiB MwRzH0UvK//oZGvSbb+Nsy/1eDHK3DuAAmo+WF9m8jrl8JTM4rUVqgJCkmouIkW9 rxSWHFvup+e4fRYLLuZqfkKOsamPRxg1at7m2L/FG0UOQGBHTjbIX6/dHM7I7Ymp VlxAv4s8wpeff/1Tm1EiDPqt/+vb/tej/VmxRS/f0Oa+gZtDx9s55hZ1WKbQO+G0 uC6jjBLCz4+eSYhXs5eRV5PUjHQoTymjeiBiwLynBWD3DGH4tt11BbysqmksrUxu FKnbDPPdyGYiuP6Ax6YC3F9dL4S+7MAxc2+pHnLHYfW4L1anvgsyRUtbwvK9LrFy bjsnJCMgIVqoJ50apPn0eOGXDVfimisCRBOBT9AhlZbG9jNXU9fnhI9zB5FZMytq HXbBLxnN0Pa3qZavLz5KTiDmoXiyXo7asoTTrnDkoyJtz8mUzGRfp8LrR8XXHJ2l Zge+3et6+2jgpGBioz/19RYpDhgHNFr8RsmDFbpofKmEi6RcEuY9p+q9JL7rHOPY +Sn/wkC9G/MsjgduyX8NT4aBOv5PjuI+evCsIebm0i1rKXkurwUMyM33nEVljNpY -----END RSA PRIVATE KEY----- And this one [file]: -----BEGIN RSA PRIVATE KEY----- Proc-Type: 4,ENCRYPTED DEK-Info: AES-256-CBC,A3BFD60060A709639D2B4D6794BA7174 CxefW9kF6wFjTqgxg2V2phMKgtmKi0UxzXGd125z8b42VQY8BnRPSlXvs/a9Kirb aKve9pW0dnQ/V0P88OvpbURjfIMfrgFJIaB1H1fcUwSxEp0zfpEcDVGFhKSIvTnf RK4ErMUV+oh21BgWSCNc6QDG5U3bt/8aXWxqqDogqKy5CUD+G4DLAi2aDe1WaPa2 9LhVp5plr/AJXRFESF3GyoFYGXNtQ3kirscSV6JOT5rQU1DnK/8XFEfexz3+iaVt Qn+AzSR52YN8PrrfFNiEF1dZWCcgS+HdyYw38IHEUpYNlFNHXSbWT+h8ml3U93wI ZtzUwSaXsT8hefUQVxFWMnO5yjkbZzA/Bgr8jFBG+Fsp8CKrnGiZH0URt6Jbt0+L Ejt/rfdYlTg8M/lsmmuncHISUcr6jGDH9uJg+7psMO9ZiUCHsSRyxUTxGvKePup9 Hc7dzr7RsMwvCo5LU4ilJRQzFwhe+V6a76xmfaTr4nzif5uuBgl7t0m4IhWedVmM 5OQOGx0QG6vX+aWzWDiXcqnxaspXW/m62E+v5QA40MzkPr7Ub6oNSh90TX9w803g WtpGolRxxsBoUfxz/5eqNDKUDZbT7o00t9djknz6Gvqg2fdtnEk014msaB0XL+uk rzLvdUohCRi0MOH63pGBPPct8iFj4/qiVeyf9nIhSk0Vw2mdcHtho9Gy4xRjDfai CXxBGVS5WotIk1rIv7ddwfAEreVllXugGeGIVt8vTt/Eb63QFGte6WOe52j2WzJg /MBWcKnL24QGD5IRA8+XdiH7TzDz4mb3cqwHlY92XL5lvlK6kJEnLWz1klCQCyOT WPiI5rB4a0gDVjYj5spBTyMnJC1D3BKEXRUJM/KzoxxYcvFqaa/lypAryrsBGep5 9KXcZoXOGHs8ldT5/hYqHWTVE6AjeO3AX+iNWbYgWgPSmeNG31HW8JStrQYW80vK PzTzS1awW1uv8RPrbJwFCHccpHXGNUNQ1dqhMD+FpNxgcHLW1DQF0+tGRd0Gm8lF Q20CmEFQS5hhyccFXO6iwmGjFEyQlxI0nsjTl+O7rjal6Yb3ZsL4KrAqbPnbO+z0 zjgOhcu4QIAGFrZR2VhiW40hfHud9RytkREP+aBgyPdNbjgsAZg7d+GewQCt8MeD XgOnIkHxet/Ib2JO40r7QR5Ru/Sz3P/z0kq+xFGwZC68jMN9FN74xATxLhvtv+ZT R9u/8hY50y3AYXyMaWIvltR8zZQhOySekU1KFUWYumrW6HCosUxEH9JuRLZzr1L6 RVClBJ2Oyfj+eILVag7FRkX0f9Vh0ECtjapp+k5jGLSXrfa5JTUI6B0JQqtc9wwT PRd3dRmuVxHSLNYVJxH5OkD+tRy3U0aeMEFXa8DXBvuM9ZJWNA7EWV2bKxMPQRok JwHPMXL859ptExBGB2C2TQFU91jVA8rQROrhAZ6O8XJsci280vWK5y0Bcxj/RabE 4hI+koFnU05rj9eQk0/B6bqDQTN/Yfi6cB8k6JsNp2qBKnpj8NLz6+UKiKJYZ1P5 o5VNQeF+OFWUzBGYqQ52NOT1pWeZZo/L3dz41eG60Hx7cSRgxzmk2na8Orn4fkbY -----END RSA PRIVATE KEY----- And this one [file]: -----BEGIN RSA PRIVATE KEY----- Proc-Type: 4,ENCRYPTED DEK-Info: DES-CBC,65DB46E90AADB85E x8fTqxWPs0RLjGud/n/Zo9HM+73Zm9WYoyG5mGI6V0BLHoTPBRCR7Px0CAav2AR1 v1r8hhXcWH21aXDeTe5D7RehvDW9WKTGRAzV/D6bVTlj3E9FblsludtLOgmW1+SS 8D+H223oBm+xF1ZpwAG+/1seltiEhTb/pED8JKkmueV+uIS2gNPmYaHtpmFZODRZ z70+m98kGiOGLOsoQyOLSFKgN8XxOH103EVw4j/bjCIqlDdl0YSAy1J/5iNsScuK cwKSl3s9bIJp9a3mOtpXufhJ6DYFbKaL09fef+mvIlHFzolVkfNsfIKuki2Eg8xY Ccxh7mVpJqj3Nfe51WdXvJdeIRA3snkfbmmZ3Nc5mmmPhE0zOf5zVPV1S7RLisP+ ZEdZgByITJI/fi4rz9S+82+oJ7vaJIggkKbraJHYDqtUZAmu1xIrN5FNjP6Tv1b4 HcQiQUiV7Qjb9yI+pP10yZ8xz6Gg/B5NQKixutLed22c7r830l8UH70vfsSbYTwc zeEXtH5EOlBrWvOfl3p5pwISfaXzRkENujzR74pLsFyClrDGTQpvACfdYM1BQvVB 5SgxXQ90oaXaFEjTJhiO/nM5a+EHwgkt486Qde0iWsJbB88KLt/tZzKl+uQehsC0 aWxPPnSfCJFnnftti4EzvSXZ5DN+o20Hf9941xq/4uJc4jUS1BIHNG8FEPdJFf6s KKRUQhHn1fWT070NDIYsF5zJP0nmuKs7Kl5fIMhTxdNonw69RZP6MBK6XvW6Dv4z yZ/s+D20HQtofZmbJdEMwdwF/qNDT7VZ3lbG/yO5qTFUyXY8PUHmqwt2l6S7CTcj LbLRx1u5HMO/begGCXMK/S4qbbtAnEasY5WBrHq5TPg6BGr/N+1gBn8D4bpPTsKP eh9KKXRhEzW0Tv0ByGP5ml4CXbG4slSS/b/vuSpU2GnFSbs3/bGgt57Lb3ge3SUw BGUOtQTUMnkq1pvakbzvxglNMDM1UoqqlL9U0yECdrGtXefAqTwYjkl6ph8iS3jR CAONvkYMIq7ifxfv5mkPTkyjNQL+8IjqhOZ/5UkN2iSojKQ4is7DRgIQUrTjmbk6 8YDPPBF5Y15z4Y7z6xWzlp+v2f8AMVdEz3XrLwEGTHETcV7nIo1zRjGZIpSqkaoJ E7L3C5OOr9mJ767ppO7QKQ1lfGaN+B75h1D9XBuwSIhgWneudmIM5DL3+fn2e/rW ozbJSR0wnO0Ueh/iBExLd1Ul/zWRJQL3Bm6QS6J01hSbrhqgil1VL0JY8Vnz0bnu kUj4bjgGeycV4xta1NatoGpfbr2QpDJgC2ShNB/iZTbTub6DrqyAuZ0BfAcLwHi2 EeQEVOudSmQeVKJbaCaSIjsd6NCW9frwSf8CRYdmc57gxuMBYTVFQaIs2UEDTH5l E8hVoK/1QP+fxIVP3ar0rr/tZKpgXSsw6SdsUrv8foP4GgY1M0lsZs210gKl+TvD DSgyj2uhSU8OyFvd0krlP7TfoPluRuiApQ2WD3oRAqUSKxi32/JwYHz/3cyWc/jp gItBrO7UK+TCRfnNrG2buxRHiWWGAcSBLTn/4uqlMQ3tOsULTq4zMJK7xH1JFfbN -----END RSA PRIVATE KEY----- The passwords are all contained within this [file] |